CYBERSEC 2022 uses cookies to provide you with the best user experience possible. By continuing to use this site, you agree to the terms in our Privacy Policy. I Agree

WeiCloud 威雲科技 Info
WeiCloud Technology started Spring of 2015. Our founding partners are experienced technology professionals with strong backgrounds in telecommunications, government, medical and corporate institutions. Together, the team has accumulated decades of information integration experience. In today’s IT industry market, clients are looking for the most advanced information security protection products tools that are supplemented with a cooperative sales channel.
Products
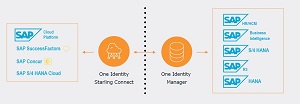
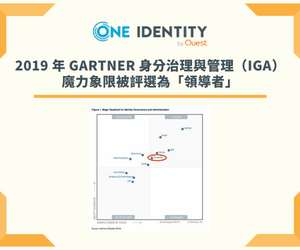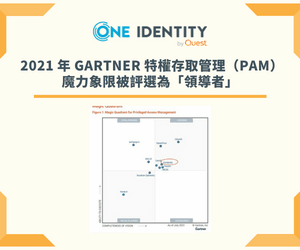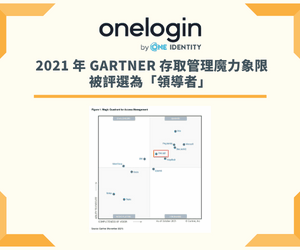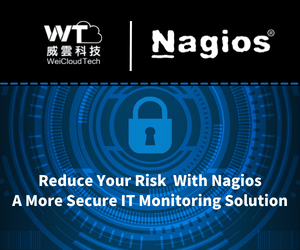
One Identity Identity and Access Management (IAM) solutions eliminate the complexities and time-consuming processes often required to govern identities, manage privileged accounts and control access. With our solutions, you can enhance your organization’s agility while you address IAM challenges from on-premises, cloud and hybrid environments.

One Identity Privileged Access Management solutions mitigate security risks and help you achieve compliance by securing, controlling, monitoring, analyzing and governing privileged access to critical organizational data and applications. Our privileged access management solutions enable you to provide the full credential when necessary or limit access with granular delegation for least privileged access. All privileged activity is recorded and all keystrokes are logged with real-time analyzation of activity and data. This eliminates shared credentials and assigns individual accountability to administrator activity with the ability to detect and halt unknown threats immediately. The result is enhanced security and easier compliance with more efficient administration and governance of privileged access.
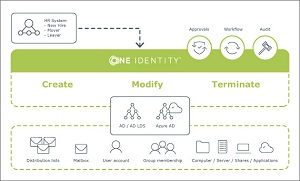
One Identity Active Roles delivers automated user account and group management that overcomes the shortcomings of native Microsoft Active Directory and Azure Active Directory tools. These enhanced identity-management capabilities enable you to do your job more efficiently, more accurately, and with less manual intervention. Active Roles is designed with a modular architecture, so your organization can easily meet your business requirements today and in the future. With Active Roles, you can automate tedious and error-prone administrative tasks and solve security issues by protecting and controlling all-important administrative access.

One Identity Safeguard can reduce the stress and worry with your privileged accounts. This innovative privileged access management solution – available as an easily deployed, hardened appliance – gives your organization a secure way to store, manage, record and analyze privileged access. It is an integrated solution that combines a secured and hardened password safe, and a session-management and -monitoring solution with threat detection and analytics. Safeguard detects and shuts down threats while satisfying your auditors and admins.

Change reporting and access logging for Active Directory (AD) and enterprise applications is cumbersome, time-consuming and, in some cases, impossible using native IT auditing tools. This often results in data breaches and insider threats to AD and other Microsoft platforms, and can go undetected without protections in place.
Fortunately, there's Change Auditor. With Change Auditor, you get complete, real-time IT auditing, in-depth forensics and comprehensive security monitoring on all key configuration, user and administrator changes for Microsoft Active Directory, Azure AD, Exchange, Office 365, Exchange Online, file servers and more. Change Auditor also tracks detailed user activity for logons, authentications and other key services across enterprises to enhance threat detection and security monitoring. A central console eliminates the need and complexity for multiple IT audit solutions.
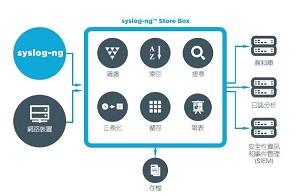
syslog-ng™ Store Box (SSB) is a high performance, high reliability log management appliance that builds on the strengths of syslog-ng™ Premium Edition. With SSB, you
can collect and index log data, perform complex searches, secure sensitive information with granular access policies, generate reports to demonstrate compliance, and forward log data to 3rd party analysis tools.
Solutions
White Papers

Identity Manager - Take the risk out of enterprise identity and access management
• Govern access to on-premises, cloud and hybrid resources from request through fulfillment for users and data
• Reduce risk by ensuring users have only the access they need
• Satisfy audit and compliance initiatives with attestation/ recertification policies
• Put access decisions where it belongs — in the hands of the business
• Build on existing investments and infrastructure and grow from there

Effective management of privileged accounts (sometimes
called superuser accounts) and privileged access is becoming more and more critical. This is because security and compliance are driving forces behind most IT initiatives and privileged rights are the key – or downfall - to achieve both security and compliance. And in today’s complex, heterogeneous environments, native privileged access management (PAM) tools and manual practices are inadequate. This white paper explores the risks associated with privileged access, and explains how solutions from One Identity mitigate those risks with granular access control and accountability.
This paper is intended for CIOs, IT directors and managers, security and compliance officers, and administrators, especially those who have not established
firm control over all of their organizations’ privileged user access.

One Identity Safeguard is an integrated solution that combines a secure hardened password safe and a session management and monitoring solution with threat detection and analytics. It securely stores, manages, records and analyzes privileged access.

With One Identity Active Roles, you can automate these tedious and error-prone administrative tasks and solve your security issues. Active Roles automates and unifies account and group administration while securing and protecting all-important administrative access. Active Roles delivers automated tools for user- and group-account management to overcome the shortcomings of native Active Directory and Azure Active Directory tools, which enables you to do your job more efficiently, more accurately, and with less manual intervention. Active Roles is designed with a modular architecture, so your organization can easily meet your business requirements today and in the future.

With Change Auditor for AD, you’ll get a normalized view of all changes and any related event details, including before and after values, as well as the correlated on-premises and cloud identities. You can also add comments explaining why a specific change was made in order to fulfill audit requirements. With Change Auditor for AD, you’ll be able to quickly and efficiently audit all critical changes to keep your valuable data and resources secure.

syslog-ng™ Store Box (SSB) is a high performance, high reliability log management appliance that builds on the strengths of syslog-ng™ Premium Edition. With SSB, you
can collect and index log data, perform complex searches, secure sensitive information with granular access policies, generate reports to demonstrate compliance, and forward log data to 3rd party analysis tools.
Videos
One Identity : A market leader in unified identity security
See how One Identity's modular and integrated Privileged Access Management (PAM) portfolio reduces complexity and operational friction to deliver just what you need in half the time and half the cost of ownership.
Learn how Privileged Management Solutions from One Identity simplify privileged account management and let you enable super-user access without putting your entire organization at risk.
The syslog-ng Store Box™ (SSB) is a high-performance, high-reliability log management appliance that builds on the strengths of syslog-ng Premium Edition. With SSB, you can search logs, secure sensitive information with granular access policies, generate reports to demonstrate compliance and forward log data to third-party analysis tools.
Whether you need to migrate to SharePoint or Office 365, consolidate your AD and Exchange environments or secure your Active Directory platform, Quest has the solutions you need. Learn more in this new video.
Nagios XI builds off the Nagios open source software Nagios Core, providing increased resources and further improvements in terms of scalability and extensibility. Nagios XI provides a central view of your entire IT operations network and business processes and monitoring of all mission-critical infrastructure components.