CYBERSEC 2022 uses cookies to provide you with the best user experience possible. By continuing to use this site, you agree to the terms in our Privacy Policy. I Agree

CyCraft Info
CyCraft Technology is a cybersecurity company specializing in autonomous AI technology. CyCraft has developed the autonomous threat exposure management platform "XCockpit," which is providing a one-stop solution for comprehensive and autonomous cybersecurity protection, and received multiple recognitions from leading research organizations such as Gartner, IDC, and Frost & Sullivan, along with numerous awards locally and internationally.
Contact Representative
- Name: Anny Tseng Channel Sales Manager
- TEL: 886-2-7739-0077
- E-Mail: anny.tseng@cycarrier.com
Products
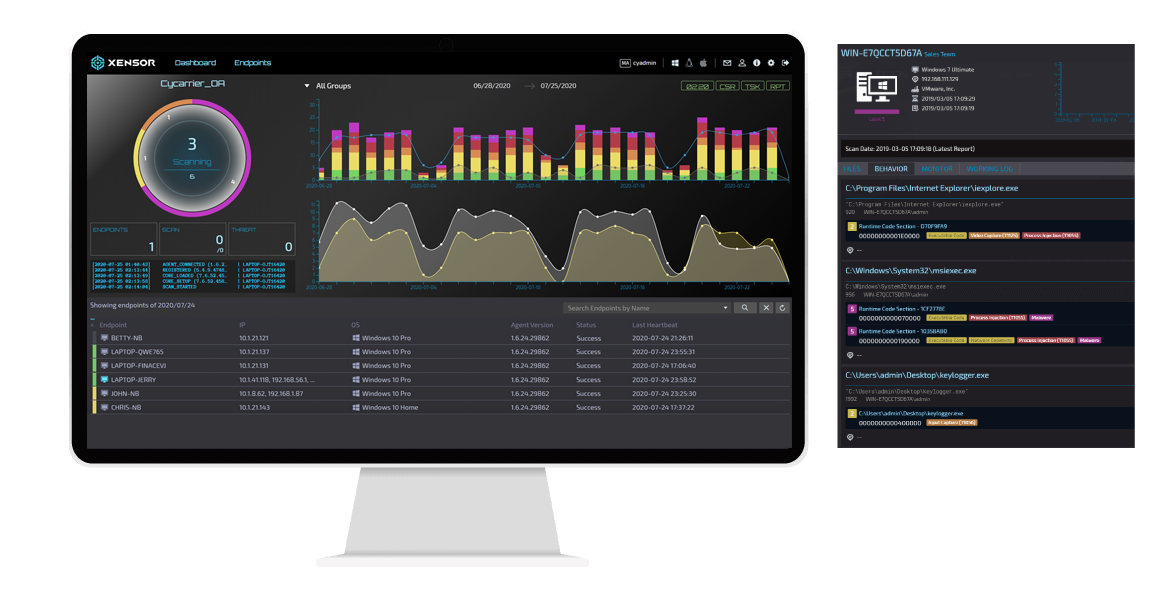
CyCraft MDR
CyCraft MDR is purposely designed to detect malicious behavior and continuously monitor and manage the cyber situation of even large-scale enterprises with thousands of endpoints. However, unlike other detection and response solutions, CyCraft MDR uniquely provides enriched intelligence and a streamlined security workflow via its fully automated and actionable dual-report system that automates investigations, triage, and response.
EDR Threat Hunting Report
Upon detection of high-risk behavior, the endpoint agent will immediately perform an automatic threat analysis and rapidly provide an EDR Threat Hunting Report, providing enriched multi-layered threat intelligence analysis and risk assessment. In parallel, the CyCraft MDR Center will perform a deep dive, multi-endpoint forensic analysis, collecting richer context information for analysis.
Cyber Situation Report
After the first endpoint threat hunting alert is issued, the CyCraft AI Analyst will begin its automated analysis, perform an all-unit trace evidence correlation, and provide a granular Cyber Situation Report, detailed multi-endpoint attack storyline, and thorough attack root cause analysis.
CyCraft MDR secures CyCraft secures government agencies, financial institutions, semiconductor manufacturing, police and defense organizations, Fortune Global 500 firms, airlines, telecommunications, SMEs, and more by being Fast / Accurate / Simple / Thorough.
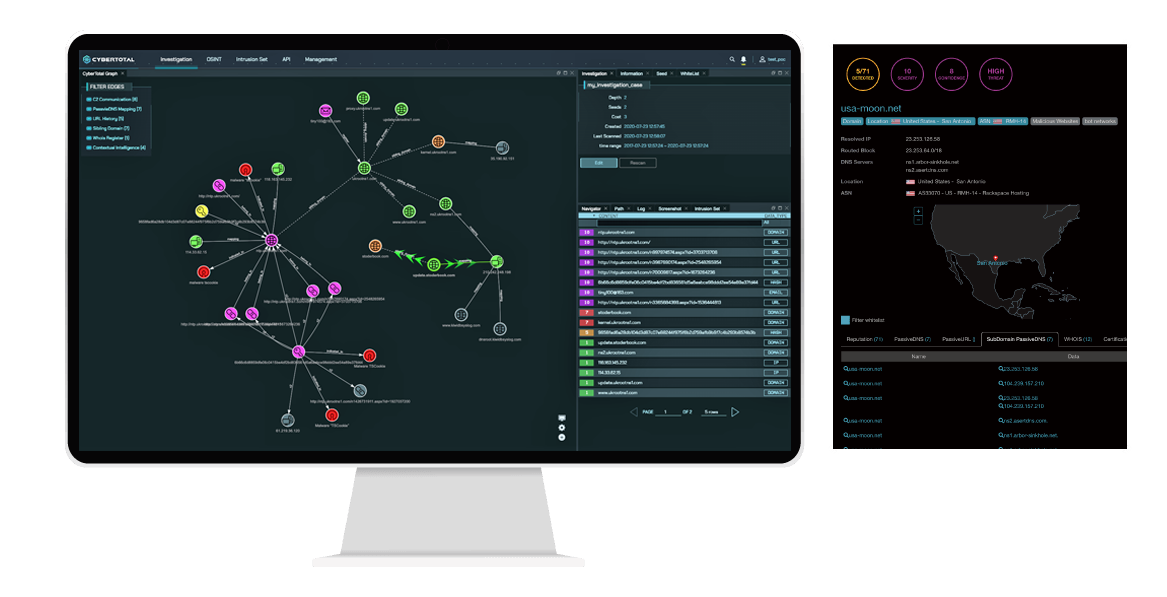
CyberTotal
CyberTotal operationalizes multi-sourced global threat intelligence on active and emerging threats in an optimal, tractable way to meet the diverse needs of organizations. While traditional cyber threat intelligence (CTI) is mainly based on the exchange of blocklists, including IP, Domain, and MD5, CyberTotal also combines enriched proprietary historical intelligence on APTs targeting the Asia Pacific region and offers rapid automated correlation analysis and severity assessments.
Highlighted Features
Convenient Integration: CyberTotal provides a complete API integration interface, quickly integrating threat hunting capabilities ideal for enterprises.
Automated Correlation: CyCraft ML-driven technology allows CyberTotal to provide rapid automated correlation analyses, high-risk rankings of severity level, confidence indices, and threat indices.
High-Quality Intelligence: Automatically integrate the latest open source and commercial threat intelligence sources from more than 130 countries around the world, and accurately label and quickly focus on critical alerts.
Standardized Intel: CyberTotal provides threat intel analysis reports in STIX 2.0 format and supports TAXII.
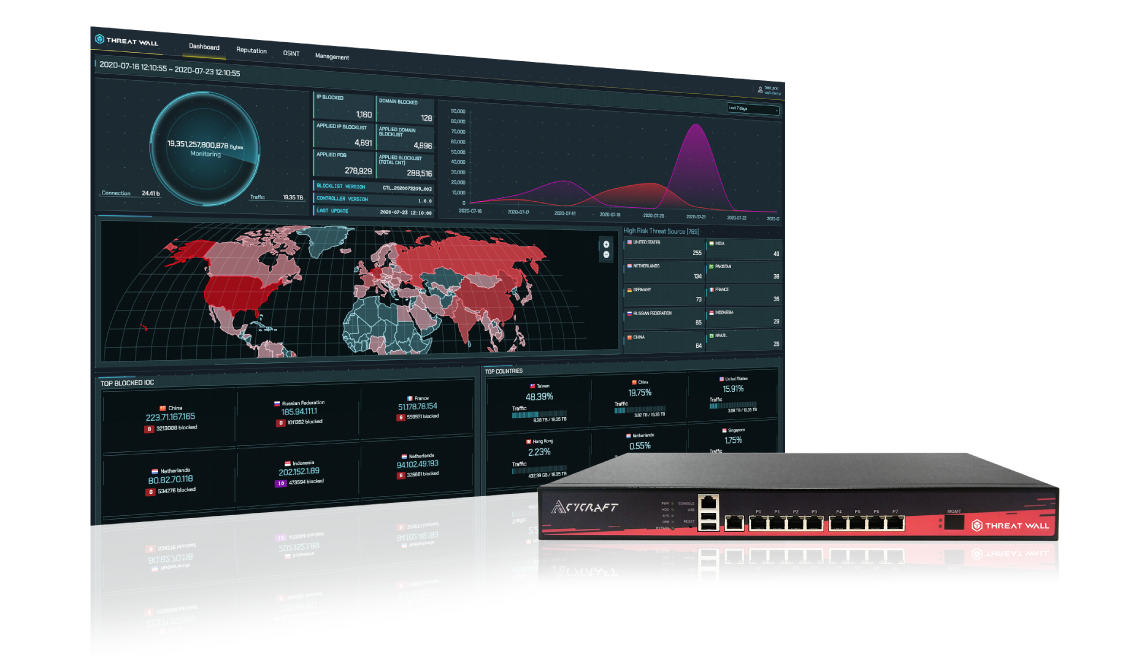
ThreatWall
The CyCraft ThreatWall Threat Intelligence Gateway (TIG) unifies automated detection and response with the latest in global threat intelligence surveillance in one multi-purpose box that stands guard 24/7/365. ThreatWall blocks both potential inbound threats from entering and compromising your environment as well as blocks outbound traffic towards any unauthorized or malicious C2 server. With its flexible and fast deployment, ThreatWall can be ready in minutes to shield and fortify your system with full-context, real-time forensics.
ThreatWall continuously scans north/south traffic for known malware, malicious IPs, and C2 servers. By integrating with our global threat intelligence surveillance platform CyberTotal, ThreatWall uniquely provides effective and efficient detection, validation, and blocking for your entire digital environment. In addition, ThreatWall can display all blocking records in real-time, provide automated reputation ratings for IPs, and supply analysts with enriched contextual threat intelligence for indicators of compromise (IoCs).
Highlighted Features
- Deployment Flexibility: Supports Inline blocking and Mirror mode to reduce the burden of infosec equipment and can support cloud or On-Prem deployment as required.
- Dynamic Updates: ThreatWall’s real-time analysis of malicious behavior and dynamic updates of blocking rules achieve an active defense and prevent zero-day attacks.
- Convenient & Flexible Integration: API and CSV download functions are provided to facilitate integration with other infosec platforms and can be customized to customer needs.
- Compliance Report: The compliance report corresponds to lists issued by various national infosec information sharing and analysis centers (ISAC).
Solutions
RiskINT
Your brand, your customers, your accounts, your data, and your infrastructure are all at risk in today’s cybersecurity ecosystem. You and your partners’ sensitive data resides on the deep, dark, and even surface web.
Every day, adversaries are buying and selling intelligence on potential targets: accounts, passwords, documents, spreadsheets, emails, as well as other data and communications.
After that, it’s only a matter of time before your intel is leveraged against you in order to infiltrate your organization, exploit it, disrupt it, and exfiltrate even more sensitive data. Risk no longer exists solely within your digital environment but beyond your firewall as well.
How do you gain visibility into the dark web, see exactly what adversaries have on you, and build an effective defense?
Gain sight beyond sight. Risk Intelligence (RiskINT) enhances proactive defense capabilities, giving you the time necessary to prepare an effective defense to better protect your brand, intellectual property, and technology infrastructure. Gain granular visibility into your leaked accounts, passwords, documents located on the dark web, and phishing domains targeting your enterprise. Be informed. Be prepared. Be protected.
RiskINT Pro: Phishing & BEC
In addition to leveraging valid accounts and leaked documents for initial access, adversaries also phish, leading to business email compromise (BEC). Phishing can come in the form of websites used to spread disinformation and damage your brand’s reputation. RiskINT Pro defends against this by providing proactive phishing intelligence. Know what domains to look out for, which ones mimic your domains, and which ones are malicious.
RiskINT Premium: Leaked Documents
Attackers use phishing emails and compromised accounts to break in often with the purpose of obtaining sensitive information. But in many cases, that information is already available on the deep and dark web. RiskINT Premium takes you behind the scenes to show you what is already out there for sale, allowing you to take action and prevent further damage.
AD Attack Path Assessment
Since Windows 2000 Server edition, the Active Directory (AD) has become one of the most commonly exploited attack vectors by cybercriminals and advanced persistent threats (APT). Access to the AD gives attackers unfettered access to your digital ecosystem, posing a serious risk to your defense posture. CyCraft AD Attack Path Assessment is a granular security assessment of your AD jointly conducted by both seasoned security analysts and the CyCraft AI Analyst.
Highlighted Features
⬥In-Depth Investigation: Analyze, visualize, and correlate abnormal relationships between AD objects.
⬥Expert Knowledge: Gain access to our team of security professionals as they scrutinize your AD security for potential, ongoing, and undetected past threats.
⬥Smart Analysis: Detect virtual groups, hidden privileged accounts, and hidden artifacts.
⬥Red Team: We calculate possible attack paths and simulate red team attacks.
⬥InfoSec Health Clinic: Assess and quantify the overall information security risk of your AD environment.
⬥Hardened Defense: Attack Path Simulation provides enhanced AD strategies to limit security threats and harden your defense posture.
White Papers

Valentine’s Day 2022 saw the end of a truly toxic relationship — a prolonged supply chain attack targeting the Taiwan financial and securities trading sector that had begun back in November 2021. Evidence uncovered during a CyCraft incident response (IR) investigation ties these attacks to APT10 — a China state-sponsored hacker group widely believed to be associated with the Chinese Intelligence Agency, the Ministry of State Security (MSS).
The November attacks were originally attributed to password mismanagement and credential stuffing; however, following a security incident response (IR) investigation conducted by CyCraft into a second wave of attacks peaking from the 10th to the 13th of February 2022, new evidence uncovered the exploitation of a severe vulnerability in commonly used financial software aided by the newly identified hacking technique, Reflective Code Loading.
The true objective of this sophisticated zero-day supply chain attack (dubbed Operation Cache Panda) does not appear to have solely been financial gain but rather the exfiltration of brokerage information, the scraping of high-value PII data (full name, home address, email, credit card numbers, passport number, date of birth, etc.), damaging the reputation of Taiwan financial institutions, and the disruption of investor confidence during a period of economic growth for Taiwan.
Videos
CyCraft MDR is forging the future of cybersecurity today by extending the frontiers of autonomous technology and human-AI collaboration. This test flight video walks you step-by-step through the CyCraft MDR user experience against a simulated ransomware attack. Gain firsthand experience into why government agencies, financial institutions, the semiconductor ecosystem, and more trust CyCraft.



