CYBERSEC 2022 uses cookies to provide you with the best user experience possible. By continuing to use this site, you agree to the terms in our Privacy Policy. I Agree

Proofpoint
Proofpoint
Proofpoint Info
Proofpoint, Inc. is a leading cybersecurity and compliance company that protects organizations’ greatest assets and biggest risks: their people. With an integrated suite of cloud-based solutions, Proofpoint helps companies around the world stop targeted threats, safeguard their data, and make their users more resilient against cyber attacks. Leading organizations of all sizes, including 80 percent of the Fortune 100, rely on Proofpoint for people-centric security and compliance solutions that mitigate their most critical risks across email, the cloud, social media, and the web. More information is available at www.proofpoint.com.
Products

The vast majority of today’s threats require humans to activate them. Ensure your users know what to do when faced with a real threat by providing them with targeted education. Our unique people-centric approach can reduce successful phishing attacks and malware infections by up to 90%. And our solution has been named a Leader by Gartner in its Magic Quadrant for 6 years in a row.

Stop threats before they reach your people and respond quickly when things go wrong. Our innovative Advanced Threat Protection solutions prevent, detect, and notify you of advanced threats – through email, mobile, social, and the desktop – and help you resolve them before they cause lasting harm.

Information protection applies security solutions and other technologies, as well as processes and policies, to secure information. Protect your information against accidental mistakes, attacks and insider risk—across your cloud services, email, endpoint, and on-premises file shares. Leverage common classifiers honed over 10 years. And achieve fast time to value and optimize your end user experience with a modern architecture that’s easy to deploy and maintain.
Solutions
PROOFPOINT EMAIL SECURITY
Proofpoint email security is a comprehensive suite of modules that enables the effective protection of organizations from email borne threats including malware, phishing, ransomware, business email compromise, email account take over, email domain spoofing and email fraud. It enable organizations to gain visibility into the threats that are directed against each employee and identity employees that are heavily attacked. In addition it correlates the risk profile, security awareness, access privileges of employees and identifies employees at risk. It enables organizations to effectively operate email security incident handling processes.
PROOFPOINT INSIDER THREAT MANAGEMENT
Proofpoint Insider Threat Management (ITM) and Endpoint DLP protects against endpoint based data loss, malicious acts, and brand damage involving insiders acting maliciously or negligently. The product correlates activity and data movement, empowering security teams to identify user risk, detect insider-led data breaches, and accelerate security incident response. Incident response teams benefit with all necessary information to analyze incidents in a single plane of glass, powered by Proofpoint's Threat Insights and data from User & Entity Behavior Analytics (UEBA).
PROOFPOINT SECURITY AWARENESS TRAINING
Proofpoint Security Awareness Training delivers the right education, to the right people for the right response to create a strong line of defense.
The solution identifies risk through revealing which users are vulnerable to attack and which users are actively being attacked. This insight into Very Attacked People (VAPs) can enable targeted training based on the threats they are being targeted with, and threat simulations using similar brands and tactics to those real-world attacks.
It delivers short, customizable education driven by threat intelligence based on the risk that a particular individual or group is experiencing and content type that suits the culture of the organization. Administrators can assign effective, entertaining training content that covers all major threat and compliance domains.
White Papers

Proofpoint eighth annual State of the Phish webinar for an in-depth look at the latest threat landscape, including phishing, business email compromise and ransomware attacks.
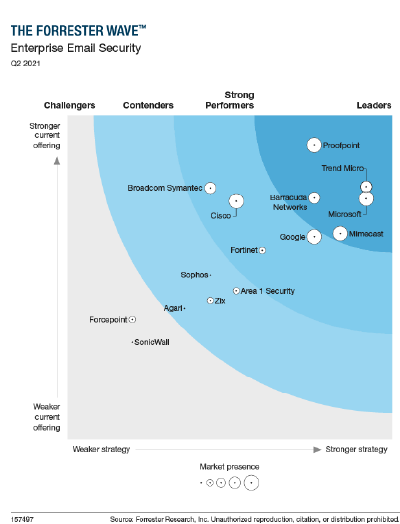
This Q2 2021 Forrester Wave Report details the top email security providers and how they stack up based on their current offering, strategy and market presence.
Proofpoint has been named a leader in enterprise email security. Using our unique Very Attacked People™ (VAP) capabilities, you can highlight who your riskiest users are. This gives you the ability to provide additional security controls and mitigate that risk.
Get your copy of the report to learn:
- Why an integrated email security solution is critical to protect your organization
- The key differentiators to look for when choosing an email security vendor
- Why Forrester recognized Proofpoint as a leader with the highest score in the current offering category

Be Ready for Ransomware
Ransomware is an old threat that just won't go away. While overall volumes have fallen from their peaks a few years ago, today's ransomware attacks are more targeted, more lucrative for attackers and more potentially damaging to your organization. Learn what to do before, during and after a ransomware attack with the 2022 Ransomware Survival Guide. You'll learn:
- How ransomware works, and how it is changing
- Preventative measures every organization can take
- The first thing security teams should do if ransomware infects users' systems
- Whether you should pay the ransom—and when not to

Cybersecurity, Ransomware and Email Fraud in a Year that Changed the World
As the global pandemic upended work and home routines in 2020, cyber attackers pounced. Dive deep into how this extraordinary time has changed the threat landscape—and what it means for the year ahead. Our premiere threat report draws from one of cybersecurity's largest and most diverse data sets to explore user vulnerability, attacks and privilege through a people-centric lens. You'll learn:
- How ransomware activity has evolved
- The latest techniques and tactics used in attack campaigns—and why they work
- How nearly every threat actor we track piggybacked the pandemic to target people
- Why business email compromise is so effective and costly
- Which threat actors persuaded more people to click

External attackers aren’t the only threats modern organizations need to consider in their cybersecurity planning. Malicious, negligent and compromised users are a serious and growing risk. As the 2022 Cost of Insider Threats: Global Report reveals, insider threat incidents have risen 44% over the past two years, with costs per incident up more than a third to $15.38 million.
Here are just a few highlights from this year’s report:
- The cost of credential theft to organizations increased 65% from $2.79 million in 2020 to $4.6 million at present.
- The time to contain an insider threat incident increased from 77 days to 85 days, leading organizations to spend the most on containment.
- Incidents that took more than 90 days to contain cost organizations an average of $17.19 million on an annualized basis.
Videos
Cyber criminals know the easiest way into your business is through your people. Proofpoint is an industry-leading security company that provides a unique, people-centric approach to cybersecurity. See how Proofpoint’s multi-layered security strategies and solutions are designed to protect your people and prevent attackers from gaining access to your networks, resources, and IP.



