CYBERSEC 2022 uses cookies to provide you with the best user experience possible. By continuing to use this site, you agree to the terms in our Privacy Policy. I Agree

ITTS Info
ITTS has accumulated over 20 years of experience in SAP ERP consulting implementation, providing IT Outsourcing and Business Process Outsourcing services. ITTS provides cybersecurity solutions, including digital banking and payment solutions, FIDO authentication, data encryption and tokenization, and etc., to meet enterprises' needs for information security services during digital transformation.
Contact Representative
- Name: Edward Wang
- TEL: 886-2-26552525 ext.610
- E-Mail: edward.wang@itts.com.tw
Products
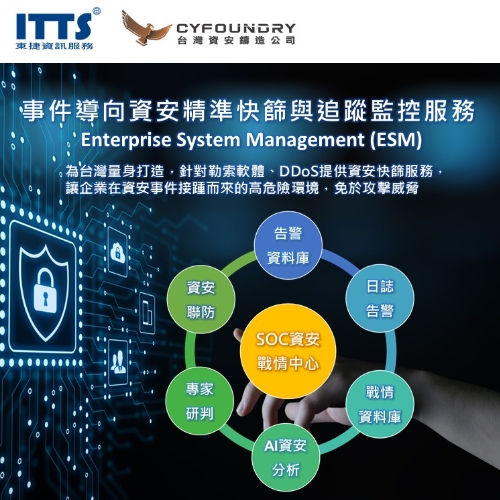
SecBuzzer ESM (Enterprise Security Management) solutions provide information security quick screening services for ransomware and DDoS, so that enterprises can avoid attack threats in the high-risk environment of information security incidents. Actively defend against information security incidents through monitoring.
Featuring cloud supply chain threat-hunting technology, we build the cybersecurity joint defense platform with precise analyzed detection, quick response and also meet the compliance regulations.
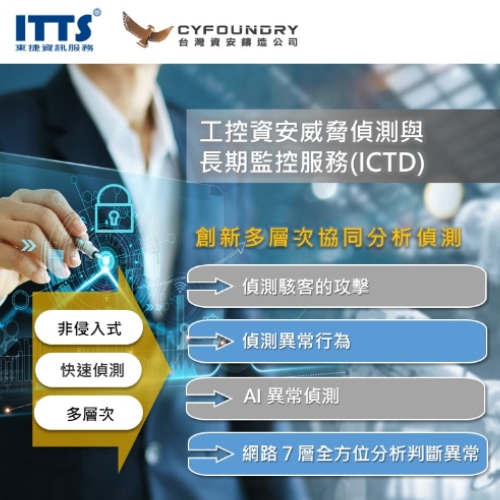
Industrial Cyber Threat Detector (ICTD) solution provides cybersecurity assessment that can help the enterprise to enhance the necessary action and improve the security protection into next level by our automated compliance assessment tool. ICTD solution can perform resource inventory for factory equipment, provide support for communication protocols across IT and OT equipment and automatically generate equipment lists, provide supply chain network topology and visualize related information security events and problems, Innovative multi-level collaborative analysis and detection, information security monitoring, and network blacklist, automatic detection of abnormalities, comprehensive observation of OA&OT network, active prevention, and create a solid network environment.
Solutions
ITTS provides professional enterprise-level cybersecurity consulting services
We provide cybersecurity detection and real-time monitoring services, from prevention, monitoring, reinforcement, response and investigation to provide a full range of information security services.
ITTS agents the cybersecurity solutions of Taiwan Cyber Security Foundry Co., Ltd. (TCFC), includes SecBuzzer ESM (Enterprise Security Management) solutions and Industrial Cyber Threat Detector ( ICTD) solution; ESM provide information security quick screening services for ransomware and DDoS, so that enterprises can avoid attack threats in the high-risk environment of information security incidents. Actively defend against information security incidents through monitoring. In addition, Industrial Cyber Threat Detector ( ICTD) solution provides cybersecurity assessment that can help the enterprise to enhance the necessary action and improve the security protection into next level by our automated compliance assessment tool. ICTD solution can perform resource inventory for factory equipment, provide support for communication protocols across IT and OT equipment and automatically generate equipment lists, provide supply chain network topology and visualize related information security events and problems, Innovative multi-level collaborative analysis and detection, information security monitoring, and network blacklist, automatic detection of abnormalities, comprehensive observation of OA&OT network, active prevention, and create a solid network environment.



