CYBERSEC 2021 uses cookies to provide you with the best user experience possible. By continuing to use this site, you agree to the terms in our Privacy Policy. I Agree

May 4-6 at Taipei Nangang Exhibition Center, Hall 2
Cyber Insight

Oliver Wu/CEO
As the pace of digital transformation accelerates, three security risks have also increased: 1. As the consumer behaviors move from offline to online, the distributed denial of attacks (DDoS) that e-commerce platforms face have reached an unprecedented peak; 2 .In response to the changes in data flow driven by the trend of office everywhere, if companies and employees do not have corresponding security awareness and actions, it will directly affect the security capabilities of the company; 3. The company begins to use automated services and reshape the network architecture to ensure that the business operation process is not. It will be interrupted due to restrictions on physical actions, and whether the security protection mechanism that arises in response is in place will directly affect the level of business risks of the enterprise.
"As the pace of digital transformation of enterprises accelerates, they begin to execute various businesses through the cloud service environment. It is an inevitable trend to use cloud services to improve and optimize corporate security protection mechanisms." Gaia Information CEO Wu Bingjun explained with DDoS attacks as an example. Consumers are increasingly relying on digital channels such as online shopping or online games. Malicious elements have begun to increase the frequency and extent of DDoS attacks. Pulsed DDoS attacks with traffic exceeding 300Gbps are becoming more and more popular. Compared with the previous passive attacks, With the help of cloud computing resources, enterprises can turn passive into active and effective defense, avoiding service interruption or the theft of smart data. "For example, we have completed relevant deployments in just half an hour to help game players block DDoS attacks with peak traffic up to 350Gbps/s, so that they can successfully complete the launch of new games."
In addition to providing companies with the ability to defend against DDoS attacks, cloud services also have four benefits. They are the use of cloud security protection services to help companies reduce the cost of purchasing software and hardware, and the use of (subscription) payment mechanisms to make companies better. The control of cash flow and the high deployment efficiency of cloud security services help to improve enterprise responsiveness. As enterprises move application services to the cloud, traditional security architectures are insufficient and must be protected by cloud security protection mechanisms.
""Information security covers a wide range of areas. Cloud security services are most suitable for defending against DDoS attacks, Bot Management attacks, and web application firewalls (WAF) that target companies’ external services. This is also Gaia Information Areas that have been focused on since its establishment in 2015.” For example, Gaia Information assists airline companies in introducing IMEPRVA’s WAF, Anti-DDoS, and Content Delivery Network (CDN) services to ensure that passengers can smoothly enter and browse websites during peak traffic. At the same time as completing the ticket booking action, it effectively defends against malicious attacks on the airline's official website and avoids problems such as information leakage.
The reason why Gaia Information is favored by enterprise customers is related to five factors, namely, it has a wealth of industrial practical experience, is comparable to international first-class talents, provides multi-cloud services, and is fast in deployment. All deployment tasks can be completed within half an hour. , And provide 7x24 Chinese/English online customer service. ""We are staffed by 40 front-line engineers to provide 7x24 online customer service. On average, a question will be answered within 15 minutes, even if customers use instant messaging systems such as LINE or WhatsApp to ask questions."" Wu Bingjun said.
The outstanding service energy not only makes Gaia Information the best partner for enterprises to build cloud security defense mechanisms, but also obtains many international original factory certifications, such as IMPERVA Taiwan’s only platinum partner, allowing Gaia Information to be the first time Obtain the latest products and resources to become the largest Anti-DDoS provider in the Asia-Pacific region, and turn passive into active defenses, such as assisting a real estate agent to block competitors from stealing hard-developed listings with Internet robots.
""We provide cloud services that include planning, construction, migration, information security, and maintenance operations."" Wu Bingjun said that Gaia Information not only acts as a proxy for many cloud platforms, such as AWS, GCP, and Microsoft Azure, but also targets public clouds. Different features and functional advantages provide customized consulting services for enterprises to accelerate the construction of new creation projects (POC) or new services. For example, the live broadcast platform can provide low-latency live broadcast services through AWS, and analyze the data viewed by users through GCP's BigQuery. The establishment of Hybrid Cloud allows enterprises to be more flexible in terms of operations and finances, and the team is more able to adjust the allocation of overall capital expenditure (CAPEX) and operating expenses (OPEX) on the infrastructure according to operational needs and IT budgets.
Wu Bingjun further explained that with the trend of enterprises going to the cloud, more and more enterprises are adopting containerization technology and starting to develop cloud-native application services. In this process, it is particularly critical to confirm the security of the code at the beginning. For this reason, Gaia acts as the world-renowned vulnerability scanning tool—Snyk. Whether corporate developers use Go, Python or Ruby for program development, they can scan the code through Snyk, analyze the relationship between the code and the code base, and keep it safe. The defensive energy extends from preventing security attacks to assisting corporate customers in scanning code security vulnerabilities.
Learn More:www.gaia.net/

2020 was considered to be a year of chaos and disaster. Big events such as the outbreak of COVID-19, geopolitical conflicts escalations in several areas, Brexit, the U.S. president election, all influenced people around the world. In 2020, TeamT5 continued help numerous security breaches caused by state sponsored targeted instruction (APT) attacks. In the meantime, TeamT5 intelligence Team proactively tracked APT actors’ new activities. Compared with real world, the cyber world was also full of turmoil in 2020 and many of them are reflections or extensions to events in real world. In this article, we will discuss our observation of APT trends in Taiwan in 2020.
In this article, we will first walk you through some remarkable trends, including:
- Evolution of APT tactic
- Supply Chain attack became a primary method in APT attacks
- COVID-19 driven cyber attacks
We will try to dissect the attacks happened in Taiwan in industrial view and adversarial view, which is a common method in threat intelligence analysis. Last part will be our conclusion and suggestions to respond with APT attacks.
In 2020, the most notable APT event in public would be the ransom-attack that strike several energy related companies in May [1]. TeamT5 research shows it to be a well-organized campaign from a notorious Chinese adversary group. Whether financial gain or political deterrence is the real motivation behind the ransom-attack remains a mystery. However, it has marked a milestone of China’s cyber-attacks against Taiwan: Chinese APT have aimed Taiwan for more than 20 years but only limited in cyber espionage operations in the past but the threat actors are now exercising new tactics to evade us.
Another cyber-attack supporting our hypothesis occurred on PTT, the most popular BBS platform in Taiwan. TeamT5 tracked a series of posts related to some scandals, with attempts to uglify Taiwanese governments or military, on PTT in July 2020. The actors abused hopping servers from various countries to hide their footprints. However, TeamT5 intelligence database shows that one of the source IP address was also used by a Chinese APT that has targeted Taiwan for more than ten years. Besides, another private source also verified the same APT group to be the culprit behind the attack. We consider both events to be indicators of China’s expansion on offensive cyber operations, which we have not observed in the past.
Supply chain attack has become a major intrusion method for threat actors in 2020 and TeamT5 had warned such tactic in advance [2]. SolarWinds breach was undoubtedly the most successful story among them. Many high-profile US government agencies, Fortune 500 companies and even cybersecurity vendors were affected. It is so sophisticated that the scope is still uncertain yet. In Taiwan, we also observed at least three waves of similar attacks that infiltrated service providers and further leveraged their products or services to infect more victims. The first two had been published by the Ministry of Justice Bureau (MJIB) of Taiwan in August [3]. The third was still under investigation and the impact could be even bigger. We have seen a significant numbers of government agencies or private corporates in Taiwan being compromised. TeamT5 research shows that at least 3 distinct China nexus group were involved in these operations.
Another interesting phenomenon would be COVID-19 related cyber-attacks. Soon after the outbreak of COVID-19 pandemic, we observed state sponsored actors collecting intelligence for the pandemic. In the second half of 2020, threat actors shifted their focus to chasing COVID-19 vaccine information with the advance of COVID-19 vaccine development. In Taiwan, TeamT5 also intercepted several spear phishing emails using COVID-19 as lure theme or even more campaigns related to healthcare related entities. We believe the trend will continue as long as the COVID-19 pandemic still exists.
TeamT5 Intelligence Team had analyzed around one hundred APT attacks from China in 2020. Our statistic shows government and military agencies are still the biggest target and attacks against them counts for more than ¼ in total and almost every APT groups that are active in Taiwan are coveting them. This trend has lasted for long since the ultimate goal of Chinese espionage operation is to obtain confidential national information. Information Technology (IT) industry also got attention a lot by APT actors and TeamT5 has observed a dramatical increase of attacks against IT industry. We believe this phenomenon is a result of threat actors’ attempts to abuse supply chain attacks and IT companies are considered to be good hopping points by actors to access various industries. The third industry being targeted in 2020 is Energy industry and TeamT5 had observed at least attacks from 5 adversary groups. It could be a sign of our adversaries’ ambitions to control our critical industries because they will be top priorities of sabotages in wartime. Education or think tanks have been long ranked as the most attacked victims because they tend to involve in classified research projects hosted by governments or political decision makings. There were several targeted attacks against companies in semiconductor industries. It makes sense since Semiconductor industry is listed as a priority to be fostered by Chinese authority in their thirteen and fourteen Five-Year projects. Cyber espionage was also adopted as a mean to improve their techniques. Healthcare and transportation are also two industries that got coveted by APT actors. As we mentioned in the previous paragraph, COVID-19 could be an incentive for APT actors to attack Healthcare industries. Lastly, we would like to raise a phenomenon TeamT5 observed: There was an adversary group which we called GouShe (a.k.a TroppicTropper, Keyboy) focus on infiltrating Transportation related entities in Taiwan. More than 70% of transportation related cases we observed were from this specific group.
TeamT5 has tracked activities from at least 9 APT groups and 8 of them are from China. HUAPI (a.k.a BlackTech/PLEAD) was definitely the most ambitious group in Taiwan. Their attacks counts around 30% of incidents we analyzed and their targeting scope includes almost all the industries we listed. The supply chain attacks we mentioned in previous paragraphs were also conducted by them. APT27 (a.k.a EmissaryPanda, IronTiger, LuckyMouse, BronzeUnion), GouShe and AMOEBA (a.k.a APT41, Barium, Winnti) are groups that are quite active in 2020. APT27 was mostly attacking government, healthcare, and financial entities. GouShe showed a peculiar interest in transportation related entities while their footprints are also observed in energy and government entities. TeamT5 has tracked this group for many years. Our research shows that the actors might bear some responsibility from their higher commands to monitor some critical infrastructure facilities in Taiwan and take control of them in case of emergency status. AMOEBA attacked energy companies, semiconductor companies, educational institutes, and IT companies. Their primary goal appears to be more for intellectual property or secret theft. But the possibilities exist that the actor might further leverage their achievement, like what they did in the ransom-attack in May. SLIME1, SLIME9 and SLIME13 are temporary code names for three Chinese APT campaigns against Taiwan that have lasted for a few years. Their activities still continued in 2020. Polaris (a.k.a MustangPanda) is another Chinese APT group that attacked almost all neighboring countries of China. We intercepted several of their spear phishing emails against government and research institutes in early stage of COVID-19 and we surmise they were gathering for information related to pandemic. One last interesting discovery: we discovered some Linux based malware used by Lazarus, a notorious North Korean APT group, circulated in Taiwan but we are unable to obtain the victim identity information. Although Taiwan is not a primary target of North Korean APT. But the Lazarus actors are believed to bear financial supporting responsibilities for their government agencies. For example, Lazarus is believed to be the culprit behind a Taiwanese bank SWIFT heist in 2017 [4]. The sample we uncovered might suggest their activities still exist in Taiwan.
The purpose of this article is to provide a high-level overview of APT threat landscape of Taiwan in 2020, since TeamT5 believes knowing your enemy is the first step of effective defense. TeamT5 research shows that APT attacks keep evolving to become very complex and impossible for a security product to defend. TeamT5 has a cyber threat intelligence (CTI) centered solution, and we rely on a dedicated team of security experts to keep us steps ahead of threat actors. Feel free to contact TeamT5 in case you want to know more about our products, solutions or discuss about threats you are facing.
[1] https://www.ithome.com.tw/news/139331
[2] https://www.slideshare.net/codeblue_jp/cb19-resistance-is-futilethe-undefendable-supplychain-attack-by-sungting-tsai-linda-kuo
[3] https://www.youtube.com/watch?v=1KXb-sf_wos
[4] https://www.reuters.com/article/us-cyber-heist-north-korea-taiwan-idUSKBN1CL2VO

In a field of cybersecurity , no matter how dedicated the security engineers are in deploying and safeguarding the defense zone. There is always a hidden and unknown adversary with unlimited resources behind the screen waiting for the good timing to strike. Giving security engineers with such a high pressure in that regards, constantly evaluating internal security defense become a must . They need to check thoroughly with management procedures, techniques , even the internal personnel in prevent any invasive entry point from the adversary and also assure that appropriate defense could take during any malicious attacks. However with such a huge flows of information , there is always a shortage of enough security engineer employees. And the work of precaution ultimately becomes the work of remediation.
Threat intelligence is the important foundation for any modern organizations.
If you could manage using threat intelligence as a defensive weapon, it will assure a reliable security for organizations as well as assisting organizations to decisively make precaution to safeguard customers, data and reputation. However, most people have the misconception of threat intelligence and the incapability of using it wisely. Most of the organization have undermined the significance of threat intelligence in that regards. As a results, they have jeopardize themselves in the ever-changing cyber world.
With underestimation, misuse, and misconception on defining threat intelligence, have turned out that it’s hard for admins to use threat intelligence properly to provide organizations regarding of the security level. If you’re lucky enough, you might capture the related threat and brag about on your monthly report. But in most scenarios, admins only received a ton of “security alerts” without making any further approaches.
Those kinds of security alerts are always presented in data formats, such as malware signature, file hash, IP, URL, FQDN or IOCs etc. Hence, it comes with manual processing data like statistics analysis of data or the activity, origin, interaction of malware report . Data like this can go with next-gen firewall, cyber defense system, anti-virus software , network devices and etc. for the sake of contributing SOC to target specific Tactics, Techniques, and Procedures in fast responding and procedure system remediation.
These kinds of data are based on security alerts can assist blocking most of the known threats as the data were collected from attacking incidents. On the other hand, having reliance on the data will eventually make security engineers to deal with too much security alerts. The process of filtering alerts can be painful and stressful, sometimes, they might miss and can’t concentrate on the real threat alerts. Also, those security alerts cannot be used with unknown attacks like zero day vulnerability. With the capability in dealing with unforeseen attack will be significant and vital.
Threat intelligence not only includes the security alerts. Meanwhile, it also provides true valuable meaning to the intelligence. Threat intelligence is a worldwide based information on collecting relevant hackers and techniques, in the use of specific attack or organization as central to offer comprehensive correlated information, as well as targeting certain organizations to form an applicable intelligence strategy. Making a thorough threat intelligence strategy can help you to be proactively to deal with different kind of threats.
The truth meaning of threat intelligence is to offer the most vital causes and consequences of the forming threat in order to improve the security defense while
enabling the resilience of organizations when facing unknown threats. As the attacking skill evolves rapidly , therefore every organization should obtain and improve their security strategy accordingly in regards of mastering the most up-to-date threat intelligence to fight against any cyber threats.
Billows Technology is well known of using threat intelligence to help customer to build the security defense line. The ISAC Wizard from Billows is a solution using security intelligence as a core defensive strategy. Through the threat intelligence shared by AT &T , it is not just a threat data or IOC, it offers a comprehensive threat attack information like the category of compromised industry. With information like that can help enterprises to deploy relevant security strategy ahead in order to block or detect the security incident. When facing unknown attack, thru Acalvio deception techniques to observe and detect unknown / Zero day invasion trajectory, as well as transfer the detected incident into threat intelligence. Billows’ ISAC Wizard not only can gather and share different sources of threat intelligence but also comply with the local regulations . Building a security incident notification system in order to help enterprise to report their incident accordingly.
For more information, please contact us.

Enterprises are more and more dependent on the network, and a single line is not enough. If the network is cut off, it will make great troubles and losses. If an enterprise is distributed in a wide area, the quality and fluency of network services are more important. How to deploy to achieve continuous connection, non-stop, improve traffic quality, it will upgrade transfer speed and reliability is more important.
Facing to rapidly develop Internet environment and business application model, UGuard AgileLink provides a management and control method, it different from the past WAN management equipment, and solves the long-time problem of poor utilization of enterprise WAN from a new perspective. UGuard AgileLink NextGenWAN Management (NGWM) equipment adopts deep packet inspection (Deep Packet Inspection, DPI) technology, which can identify more than 2,800 applications and more than 50 web page categories, allowing administrators to differentiate, from the perspective of implementing the resource allocation of circuit bandwidth, it breaks the traditional practice of using only source and destination network addresses.
Software-Defined WAN Management
UGuard AgileLink has launched the new WarpTunnel™ function, which facilitates managers to consolidate multiple lines into virtual connection bandwidth between multi-point offices, improving the rate, stability and quality of critical traffic transmission. When there is a line failure, AgileLink will automatically select a better quality line for data transmission. Ensure that at the moment of failover, even if the user is using the Internet phone, there will not be any interruption or delay.
In addition to Internet access and multi-point office connection quality, maintaining corporate open services is also an important point that cannot be ignored. UGuard AgileLink has a line status detection function. When the service line status is abnormal, AgileLink will automatically direct the service traffic to the normal line to prevent service interruption and cause business operation losses. Through the technical integration of domain name resolution and line status detection, the continuous operation of corporate services is effectively maintained.
Multinational Routing Service (UCloud)
The point-to-point VPN connection solution requires different considerations at home and abroad. International connections need to consider the connection policy of each country or the issue of line stability to ensure that important corporate services can be stable, effective and quickly transfer. AgileLink's UCloud service considers the international connection specifications of various countries for you in advance, and uses Software-Defined technology to maintain the quality and stability of the cross-border backbone circuit, ensuring the connection speed you purchase and the actual use Quality is guaranteed.
Automatic Event Response
Innovative event prevention mechanism, effective and automatic preventive measures are taken before you notice the occurrence of the event to prevent the continuous expansion of the event and affect the corporate network. Unlike traditional management solutions that focus on allocation and restriction, and cannot actively detect the precursors of the gradual expansion of events, UGuard AgileLink provides you with a flexible adjustment mechanism that automatically detects changes in the number of connections or bandwidth usage caused by abnormal behavior. Take corresponding restrictions to prevent the occurrence or expansion of the incident. When AgileLink's management interface prompts you the source of the problem, it is the result of the system taking care of the problem for you, which greatly reduces the burden of logging in to the management interface to find the source of the problem and deal with it one by one and improve management efficiency.
Historical Statistics Report
UGuard AgileLink provides a built-in historical statistical report function, so you don't need to spend extra to purchase statistical report information. No matter how good a control and detection solution is, historical records and statistical information are indispensable. AgileLink provides you with a complete solution. Whether it is line management, flow control, and anomaly detection, it also has built-in historical statistical report information. You can obtain all historical records and statistical information on the device to confirm the past corporate network usage status. Information such as Top N's access source, application usage, or access domain can be found in the built-in reporting system. At the same time, the built-in report also provides related statistical information and export functions, allowing you to easily click on the query conditions you want to apply and export detailed statistical data when you query the report.
Features :
1. WAN Access Load Balancing (support In / Outbound Multi-Homing)
AgileLink can provide the diversion function (L7 identification) of the application service, and can combine the line bandwidth so that the traffic can be effectively distributed to each line.
2. Circuit Detection and Failover
AgileLink can support more than 8 load balancing calculation methods, flexible and effective allocation of line priority order. Not only provides line health detection, but also provides a backup mechanism to ensure network stability.
3. Bandwidth Control of Apps and Websites
Built-in more than 2800 kinds of application and website identification database, effectively control network bandwidth.
Large-volume services such as video conferencing and Internet telephony can be allocated to lines with ample bandwidth to ensure that important services are not interrupted.
4. SD-WAN International Line Service
In addition to the commonly used MPLS and cross-border dedicated line services, AgileLink provides more cost-effective international line services, and has a complete platform to uniformly control line usage, reduce operating costs, and provide the best backup helper for companies to integrate internationally.
5. Application Identification Function
・Recognize 2,800 apps
・Built-in more than 50 web types
・Customize application features
6. Line Management Function
・Multi-line bandwidth consolidation
・Multi-line load balancing algorithm
・Line health detection
・Source address policy routing
・App policy routing
・Web address policy routing
・Built-in domain name query server
・Multi-Homing
・Resource Record (RR) Health Detection
・Resource Record (RR) load balancing
7. SD-WAN
・Multiple VPN connection integration
・Connection quality detection
・Connection health check
・Connection failover
・Redundant data transfer
・Packet delivery load balancing
8. Automatic Event Response
・Connection detection
・Bandwidth usage detection
・Cumulative usage detection
・Duration detection
・Cumulative time detection
・Flexible automatic time limit
・Enhanced automatic time limit
9. Historical Statistical Information
・Equipment resource history information
・Network interface traffic history information
・Top N usage sources ranking
・Top N application traffic
・Top N domain connection rankings
For the latest information on UGuard, please follow UGuard Taiwan website, and Facebook @uguard888

BeyondTrust experts, Morey J. Haber, Chief Technology Officer and Chief Information Security Officer; Brian Chappell, Director, Product Management and Karl Lankford, Director, Solutions Engineering forecast the future threat vectors that most likely to affect organizations worldwide in the New Year. These projections are based on shifts in technology, threat actor habits, culture, and decades of combined experience.
Prediction #1: The Hacking of Time -- Network Time Protocol (NTP) and Windows-time-based servers will become a protocol of interest to hackers. These protocols help control the timing of everything transaction-based within an organization. If the timing is off, everything from licensing servers to batch-based transactions can fail, creating denial of service attacks in key infrastructure on the Internet and within the backend processes of an organization.
Prediction #2: Poisoning of Machine Learning Training Data -- As machine learning becomes more widespread within enterprises for making automated decisions, attackers have a new vector to consider. After a threat actor steals a copy of the original training data, they will begin to manipulate the models generated by injecting poisoned data into the training pool, creating a system that has learned something it shouldn’t. This manipulation will have a multiplying effect due to the automatic processing by downstream applications, destroying the integrity of any legitimately processed data.
Prediction #3: Weaponized AI, Now Just Another Tool in the Attacker Toolkit -- Threat actors will leverage machine learning (ML) to accelerate attacks on networks and systems. ML engines will be trained with data from successful attacks. This will allow the ML to identify patterns in the defenses to quickly pinpoint vulnerabilities that have been found in similar systems/environments. Data from all subsequent attacks will be used to continue to train the cyberattack engine. This approach will allow attackers to zero in on entry points in environments far more quickly and stealthily as they will be targeting fewer vulnerabilities with each attack, evading tools that need a volume of activity to identify wrongdoing.
Prediction #4: Deepfake Everything -- Expect to encounter a new wave of deepfakes that challenges us to believe whether the entity on the other side of an interactive chat window or video call is human or not. For instance, you could soon have interactive sessions with past presidents or even deceased love ones. We will increasingly be in situations, unbeknownst to us, where we are engaged in communication with deepfake technology rather than with a real person.
Prediction #5: Cyberattackers Set up Shop at the Network Edge -- New attack vectors will target remote workers and remote access pathways. Cybercriminals will continue to wage social engineering attacks and also try to exploit common home devices that can be used to compromise an individual and allow for lateral movement into a business. Social engineering attacks will primarily involve various forms of phishing, including by email, voice, text, instant messaging, and even third-party applications. We foresee remote workers to reign as the number one attack vector for exploitation in 2021.
Prediction #6: Data Privacy Implosion -- In 2020, the European Union (EU) court system overturned the governance for protection provided by the EU-U.S. (United States) “Privacy Shield.” Throughout 2021, businesses will scramble to adapt to this expansion of data privacy regulations and the potential implosion of established policies based on challenges in the court systems. International businesses will have to adapt quickly to reengineer how they process client data. Businesses that operate in multiple states must consider how they manage data per state, process it in a centralized location, and codify how they develop procedures around data deletion and breach notification.
Prediction #7: Social Media Attack Vectors Thrive in the Era of Social Distancing -- Expect attackers to move beyond just targeting individuals through social engineering to targeting businesses as well. Poor authentication and verification practices will allow social media-based attacks to be successful. Malicious QR codes or abbreviated URL’s could also be employed to obfuscate the malicious website. Since the social media controls around posting, verification, and URL redirection are so poorly managed, expect new attacks to flourish.
Prediction #8: Cybercriminals Play Puppet Master with Compromised Human Identities -- To reduce the cost of an attack and improve profitability, cybercriminals will target individuals directly to gain an initial foothold in the environment by using non-cyber forms of coercion (bribery, extortion, etc.). These attacks will primarily focus on public figures (politicians, actors, activists, executives, etc.). As more of the human target’s sensitive personal data is stolen digitally, the pressure will mount for individuals to carry out nefarious actions or have their data and privacy exposed to the public.
Prediction #9: Cyber Insurance becomes Mandatory—Cybercriminals Rejoice -- Cybercriminals will target large brands with insurance policies. The insurance policies will pay out to release stolen data rather than face paying out on the policy to cover any remedial action, providing attackers with a new stream of income.
Prediction #10: Who goes there? Friend or Fake? The Rise of Identity-Centric Security -- As systems and services move out of the traditional network/data center environment, security leans more heavily on proof of identity. A verified identity could now be the only ‘key’ needed for all access. Attacks on the mechanisms that maintain and secure verified identities will increase through 2021 and beyond.
For more information, please visit: https://www.beyondtrust.com/press/beyondtrust-releases-cybersecurity-predictions-for-2021-and-beyond.

Research states that more than 40% of people abandon a website that takes more than 3 seconds to load, and the average cost of a DDoS attack is USD120K. As you can see, having a solid performance and security solution in place is quite essential if you aim to stay in e-business.
The world is moving online at an ever-increasing pace. Online shopping, business transactions and the amount of online content engaged with has seen an incredible rise of the past few years.
In this modern digital world, e-businesses realize that it is important to provide a safe and fast user-experience to their website visitors if they wish to prevent the devastating consequences of slow loading web pages, cyber attacks and website outages. Hence, they go to great lengths to optimize website performance and security.
mlytics features an AI-based Multi CDN platform that provides a cost-effective, easy-to-manage solution for businesses who seek to enhance the security and performance of their website.
The mlytics Multi CDN system grants businesses access to top-tier CDN providers around the world to guarantee better performance. It constantly collects latency and availability data to autonomously route traffic to the best-performing CDN via AI and deliver the best possible customer experience for one’s domain. Thus, traffic spikes and fluctuations don’t affect a website’s content.
But more importantly, the mlytics Multi CDN solution offers enhanced security features for its customers. For example, in case of a DDoS attack all malicious requests targeting L3/L4 that aren’t accessing via port 80 and 443 will be filtered out automatically for users due to the fact that CDNs strictly only allow port 80 and 443 accesses. Even if there are port 80 or 443 malicious requests, the bandwidth which Multi CDN provides is large enough to absorb most of the attack.
As for L7 attacks, mlytics uses its own advanced DDoS protection technology to unify the security policy and keep users’ origin server protected. We offer multiple L7 DDoS attack mitigation methods, including block scanner, block crawlers, browser integrity check, and challenge & response. Most application layer attacks are mitigated automatically by default.
As mlytics is using the Multi CDN to absorb requests, both security and performance can be guaranteed anytime without one sacrificing the other.

Since the U.S.-China trade war and the pandemic of COVID-19, the world’s conflicts have been increased are not only in economic or public health, but also in cyber technology. Last year, president Tsai vowed that cyber security is a part of national security, and invest significant human resources and money for development. It is obvious that the importance is upgraded to core national strategy level.
Threats come from different aspects, such as exterior network attacks, phishing and ransomware, and interior conspiracy. In the past year, Taiwan suffers nearly 3 times more networking attacks than other Asian countries. The frequency is so high that the government and enterprises must keep alerted 24 hours non-stop, causing IT managers’ tremendous workload and pressure. Data leak events happen from time to time. The sold privacy data might be used for fraud crimes. People’s property are damaged and so the reputation of the responsibility party. The theft of intelligence property might even undermine the country’s power and influence. Cyber security has become the first priority and every organization is patching up vulnerabilities in order to lower down risks it could bring.
For every invasion, there must be a goal. It could be a pure exercise or a psychological warfare. But the worst case is some interior worker take the advantage of networking attack events and transfer massive sensitive data under the table. This kind of data leak is hard to detect because when an attack starts everyone is focus on finding out the source and stop it from spreading. The easiest way to kill virus is to format the system and restore to the origin. However, at the meantime, all logs and traces are cleaned and you have no clue to put the pieces together any more, and the vulnerability stays hidden so that it might come back the other timer. In a long term, the core competitiveness keeps losing and the leading position could be taken.
Talking about the defense side, the key task is Do Not let your opponent get what they want. If invasion is inevitable, whether it comes from the outside or insiders, plan B is essential to strive for more time and mitigate damage caused by data breach. So what preparation can we do? We would suggest building multiple safety net to catch every possible loss. The first layer is to collect logs and evidences as much as possible. So even the attacked PC is restored, the activities can still leave traces so that you can see how things happened. The second layer is risk foreseeing and real time alert. With the abnormal figures in reports you can sense the storm and so necessary measures can be taken in advanced. Along with alert setting, when things go wrong you can react in the first place. The third layer is file backup. It’s not limited to ordinary daily file backup. Furthermore, if deleted files can also be collected and retained, investigation will be faster. The forth layer is to encrypt important files, no matter personal privacy data, confidential documents and drawing. As a result, even they are transferred to other places, the content remains protected. A great deal of time and effort of mess cleanup can be saved. Adopting multiple safety measures as precaution give you some immunity when facing data theft or attacks.
Secward Technology’s newly- launched file protection software goPatrol is just designed to provide multiple safety measures. There are 6 function categories: file logs and output control, report and alert, software asset management and control, hardware asset list and external device management, file clone, and file encryption. These functions are not just put together and work independently, they are integrated horizontally for the purpose of data protection. Taking logs for example, every operation related to a file, including rename, share or printing, are collected to one log query table. Administrators can filter the records by a user name, operation type, or even the text of confidential technology or customer name. Then, click on the record details to look into the file content. You don’t need to switch among modules to analyze printing logs, IM logs, file logs and monitoring video to find out the whole picture. They are put together for the purpose of efficiency and evidence reliability.
The applications and services will grow explosively following the development of 5G, IoT, and AI in the foreseeable future. The trend no doubt will expose more and more vulnerabilities of whatever connect to the networks. The more you embrace new technologies, the more security control is required. goPatrol build up versatile protection to fulfill the requirement of safety, management, and inspection. When tsunami comes, only those who are well-prepared can get out without hurts.

CrowdStrike is the leader in cloud-delivered next-generation endpoint protection. CrowdStrike has revolutionized endpoint protection by being the first and only company to unify next-generation antivirus, endpoint detection and response (EDR), and a 24/7 managed hunting service — all delivered via a single lightweight agent. The CrowdStrike Falcon™ platform, certified to replace legacy antivirus, has reinvented how endpoint security is delivered with its industry-leading, cloud native architecture.
CrowdStrike Falcon protects customers against advanced cyber attacks, using sophisticated signatureless artificial intelligence/machine learning and Indicator of Attack (IOA) based threat prevention to stop known and unknown threats in real-time. Core to its innovative approach is the CrowdStrike Threat Graph™ which analyzes and correlates over 50 billion events per day from millions of sensors deployed across more than 170 countries, uniquely providing crowdsourced protection for the entire customer community.
Many of the world’s largest organizations already put their trust in CrowdStrike, including three of the 10 largest global companies by revenue, five of the 10 largest financial institutions, three of the top 10 health care providers, and three of the top 10 energy companies.

This year (2020), “Digicentre” is the only enterprises that won the cloud information security award from the international standard authority -- British Standards Institution (BSI), and was invited to participate in excellence organization recognition ceremony of the “2020 BSI InfoSec Standards” held by BSI to receive the award. Why was Digicentre the only enterprise that won this award, and what services did they provide to help the local enterprises in Taiwan?
The special background of Digicentre: Existing services and competitive advantages
“Digicentre” was formally the IDC, information security, system and network business department of Gamania, and is now the joint venture company of two listed companies, Gamania and Mercuries Data Systems (MDS); its technical team has 19 years of server operation experience.
In recent years, in order to serve high-end customers with differentiated products, Digicentre gradually transformed from a traditional Internet Service Provider (ISP) to Managed Service Provider (MSP), and its products expanded from Infrastructure as a Service (IaaS) to “Information Security as a Service” Software as a Service (SaaS).
In order to strengthen the security of cloud services, Digicentre not only imported the ISO 27001 information security management system, it also focused more on the security control of cloud services, including formulating cloud service security policies, establishing various security goals, implementing security control measures, performing educational training plans to raise the information security awareness of employees regularly and implementing the ISO 27017 and ISO 27018 cloud service information security and personal information protection international standard verifications gradually. By passing third-party verifications and obtaining certification from BSI, combined with its local advantages and industrial experiences, Digicentre is able to provide comprehensive help to Taiwan’s enterprises.
The manager responsible for this project and lead the company to win the reward, CHIN CHIH HAN, stated that: “passing the verification is only a phased task, information security is the responsibility of every person in the enterprise that must be executed and focused on continuously in order to implement properly. In the future, we wish that Digicentre can expand the verification range and import other standards, and become the leader in relevant industries.”
Editor’s Note: The British Standards Institution (BSI) was established in London by the Institution of Civil Engineers. It is the world’s first international standard institution and the only one established by Royal Charter, now called “BSI Group.” The well-known “ISO 9001 Quality Management system” and “ISO 27001 Information Security Management System” originated from BSI.
Rushed to the cloud by the pandemic but full of loopholes? Digicentre can help!
This year, due to the pandemic's impact, many enterprises were forced to accelerate digitization and rushed internal operating procedures or external customer services to cloud. Since it was sudden, usually there was no time to take information security into consideration. Digicentre provides online real-time information security services that are able to quickly detect information security risks and defeat them one by one, allowing enterprises to use the easiest and fastest ways to protect the data of the company and customers.
Digicentre provides information security service cloud solutions, helping customers protect information security comprehensively from two aspects:
1. Cooperating with SecurityScorecard (SSC) to provide 7x24 monitoring service of information security risks 365 days a year, displayed to customers in a dashboard form and allowing administrators to quickly grasp the real-time statuses of the various aspects of information security.
2. The use of the “Digicentre Multi-CDN Platform” can defend against common external threads, such as DDoS and DNS attacks etc.; layer 3, 4 and 7 protection functions are provided for DDoS and other types of protection such as WAF as also provided.
SecurityScorecard (SSC) -- American information security cloud platform
Digicentre has provided information security services to the financial industry and SMBs for many years in the past and has transformed to professional Managed Security Service Provider (MSSP) recently. This year, it also became partners with SSC.
SSC is an American information security cloud platform; many large foreign enterprises such as Intel, Google, Nokia, AXA, Disney and Moody’s etc., as well as some of Taiwan’s large indicator companies such as the semiconductor industry and the financial holding industry have also joined the ranks of using SSC.
SSC uses big data and smart algorithms to accurately categorize the different types of information security threats and eliminate noises and false positives. The different types of risks include endpoint information security risks, network information security risks, patch cycle and malware IP connection messages (including malware and spam) etc. It also uses 10 key factors of information security risks to calculate the risk levels, then combines them with the big data previously mentioned. It then uses advanced machine learning algorithms to predict whether the enterprise will become the victim of data leakage. The SSC monitoring platform works all year round; whenever new threats are generated, warning notifications will be sent immediately.
Enterprises that use SSC services can directly coordinate and communicate with third-party ecosystems on the SSC platform; the intuitive user interface allows customers to easily manage the network environment ecosystem's security. What SSC achieved is not only an information security risk assessment platform but also an accurate network information security risk management system that can be used flexibly.
Digicentre Multi-CDN Platform
Since there are many CDN brands on the market, users must be familiar with each brand's attributes and advantages to find the CDN that matches their needs the most, which makes it quite troublesome for maintenance and management.
Digicentre Multi-CDN platform provides “one-stop CDN platform management” services, allowing users to manage various CDN suppliers on the Digicentre platform, including Akamai, Verizon, CloudFlare, and other well-known CDN brands. There’s no longer the need to waste time exploring, comparing and managing many CDN services; they can be used simultaneously to fully exert the advantages of the different brands.
Users of the Digicentre Multi-CDN platform can configure multiple CDN services simultaneously, along with suitable services and backup mechanisms, and switch to the best CDN service automatically according to the monitoring quality through the platform’s AI Load Balancing mechanism and the RUM (Real user monitor) smart monitoring.
Digicentre’s CDN platform upholds the SaaS service feature, giving users highly free and autonomous management privileges to add or adjust CDN needs manually at any time. When temporary changes are caused by business needs, users will not be troubled by service contract periods etc., controlling costs effectively.
In addition, the platform can recommend suitable CDN suppliers based on the location of the user. For example: local CDN brands such as ChinaCache and Wangsu can be used in the China region.
Digicentre has your back in the cloud era!
In response to the digitization of enterprises, more and more enterprises moved their data onto the cloud; it is an irreversible trend that developed even faster due to the pandemic's impact this year. The future will be an era where everything is networked everywhere; maintaining the stability of cloud data and protecting cloud information security will become keys to whether enterprises can develop and grow in the cloud era for a very long time.
Digicentre Multi-CDN platform has the flexibility that a single cloud service cannot guarantee. It hosts the American SCC’s real-time assessment of information security risks, able to reduce related worries significantly a comprehensive cloud partner of enterprises.

Many attempts to establish seemingly unnecessary procedure, which is usually labeled as “red tape” in governmental entities or enterprises, are in large part to place trust and ensure accountability. In case something unexpected or violations occur, there is someone to be blamed and held accountable.
The situation gets even worse in the digital world. Digital bits are invisible. We do not know whether malicious contents sneak in under the cloak of legitimacy. In this regard, we use accounts and passwords, SMS, policies and others to confirm identities. Verification is doubtlessly required, but as there are more and more accounts and passwords to memorize and nastier cyber and phishing attacks, enforcing harsher password policies resembles a hamster on a wheel. A report even shows passwords are the root of 81% of breaches. Only by thinking beyond the frame can we devise a way out.
Paradigm Shift in Trust
With passwords jeopardizing productivity and security, a paradigm shift toward the PKC‐based (public key cryptography) trust anchor has occurred. We no longer place trust in passwords. Rather, we place trust in cryptography; we place trust in a private key securely stored in a secure environment and never leaving its physical secure boundary. For more information, check out FIDO Alliance.
WiSECURE AuthTron enables painless fido (Latin: trust)
WiSECURE Technologies’ AuthTron product series is U2F and FIDO2 certified. It either supports password‐less login or heightens existing authentication methods relying on passwords.
On top of it, with WiSECURE expertise, we extend it beyond authentication. The built‐in crypto engine also supports encryption, digital signature, blockchain applications and others. For use cases, check out other videos in our channel.
In January, WiSECURE Technologies joined FIDO so as to develop password‐less multi‐factor USB keys. We aim for
- Comprehensive product portfolio
- Post‐quantum cryptographic implementation
- Cognition‐based/Behavior‐oriented verification

Entrust a global leader in trusted identity, payments and data protection, in early Jan this year announced that it has acquired HyTrust, Inc. an innovative provider of virtualized and multi-cloud data encryption, key management, and cloud security posture management solutions. Terms of the deal will not be disclosed. By acquiring HyTrust, Entrust adds a critical management layer for encryption, cryptographic keys, and cloud security policy to its digital security solutions, serving the data protection and compliance needs of organizations accelerating their digital transformations.
“Enterprises are rapidly transforming to take advantage of the efficiencies and scale of cloud computing. In doing so, data protection and compliance are top of mind. That’s why we are excited to bring the HyTrust team and solutions to Entrust,” said Todd Wilkinson, President & CEO, Entrust. “HyTrust solutions help enterprises manage, automate and scale security controls across computing environments. Now, customers can turn to Entrust as a single source for high-assurance data protection, identity and compliance solutions that allow enterprises to encrypt data and enforce security policy across virtualized, public and hybrid cloud environments.”
Based in Mountain View, Calif. and founded in 2007, HyTrust solutions automate security controls for software-defined computing, networking, and storage workloads to achieve the highest levels of visibility, granular policy control and data protection. HyTrust customers can accelerate cloud and virtualization cost savings while improving their security posture through real-time automation and security policy enforcement; adapting quickly to compliance requirements; and preventing unplanned outages. HyTrust partners include VMware, IBM, Cisco, Intel, Google, Amazon, and In-Q-Tel. The privately held company has approximately 50 employees who will join Entrust with the acquisition.
“We are extremely pleased for HyTrust to join the Entrust team. Entrust is an established leader in data protection, identity and payment security solutions, with the crypto expertise and global reach to expand and support our solutions around the world,” said, Eric Chiu, co-founder and President of HyTrust, who joins Entrust as part of the acquisition. “As multi-cloud deployments become more commonplace, organizations struggle to protect cloud infrastructure and data. Our integrated solutions enable enterprises to harness the power of cloud platforms without sacrificing security and compliance.”
Entrust and HyTrust have partnered on joint solutions that combine Entrust nShield® hardware security modules (HSMs) with HyTrust DataControl and KeyControl cryptographic key management servers (KMS). The joint solutions centralize and automate cryptographic key management, enabling enterprises to consistently generate and control encryption key lifecycles at scale. With this acquisition, Entrust plans to accelerate security and compliance solutions for on-premise, hybrid, virtualized and multi-cloud environments.
“Having expertise in data encryption, key management and cloud security policy under one roof delivers powerful benefits to our collective customers – improving their security posture and meeting compliance requirements while simplifying encryption and key management across environments,” says Cindy Provin, Senior Vice President and General Manager, Identity and Data Protection, Entrust. “We look forward to working with the HyTrust team, its partners and customers.”
For more information about the HyTrust acquisition, visit https://www.entrust.com/partner-directory/hytrust.
About Entrust Corporation
Entrust keeps the world moving safely by enabling trusted identities, payments and data protection. Today more than ever, people demand seamless, secure experiences, whether they’re crossing borders, making a purchase, accessing e-government services or logging into corporate networks. Entrust offers an unmatched breadth of digital security and credential issuance solutions at the very heart of all these interactions. With more than 2,500 colleagues, a network of global partners, and customers in over 150 countries, it’s no wonder the world’s most entrusted organizations trust us. For more information, visit www.entrust.com.

In 2020, we saw cyber-criminals take advantage of collective uncertainty with ‘fearware’ phishing attacks, and continue to shrink the lifespan of their attack campaigns by purchasing cheap domains in their thousands and regularly updating their attack infrastructure. As organizations began to rely heavily on SaaS collaboration tools, we also saw a marked increase in account compromise and phishing from the inside.
What new tactics and techniques can we expect email attackers to deliver this year – and how will companies react? This blog presents five predictions for security teams to keep an eye on in 2021.
1. Supply chain fraud will overtake CEO fraud
Targeting the C-Suite is a well-known tactic that has brought attackers success due to both the sensitive and valuable data these executives are exposed to and the authority they hold within a company. But with special protections increasingly put in place, it can be hard for an attacker to get to these individuals. The alternative for attackers? Go after whoever an organization trusts.
When an attacker can take over the legitimate email account of a trusted third-party supplier, they can net a big return without ever interacting with a C-level executive. Because of the implicit trust between established contacts, it’s likely that suppliers and contractors with large client bases will become ever more tempting targets. Why work hard to compromise 500 companies separately, when you can compromise just one and send fraudulent invoices to a thousand?
There are signs already hinting in this direction. Research earlier this year found that spoofing attacks that target the C-suite were decreasing. Meanwhile, the high-profile SolarWinds hack has shown just how effective cyber-attacks that come through the supply chain can be.
2. Email security solutions and third-party gateways that deploy via MX Records will be phased out
This is not so much a threat from attackers themselves, but rather a risk posed by existing email security tools – in particular, how they are deployed. Many email security solutions and third-party gateways currently sit right within the mail flow, directing traffic by way of mail exchanger records (MX records), which specify the mail server responsible for accepting email messages.
The trouble with this method isn’t really a security problem: it’s an operational issue. If the security tool sits within the mail flow, it can become a potential obstacle. If something goes wrong with the security gateway – an outage, for example – it can disrupt, or block, the entire flow of mail.
This disruption to business inevitably results in heightened pressure on security teams. Even when fully functioning, this deployment method can introduce latency, which is becoming less tolerable as remote work becomes more prevalent.
For this reason, we’re likely to see security teams continue to shift away from this deployment method, to API-based solutions that don’t require configuration changes and alleviate the risk of downtime.
3. The email attack cycle will continue to shorten
Once upon a time, attack infrastructure lasted for weeks or months. Darktrace research found that the average lifespan of fraudulent email dropped from 2.1 days in March 2018 to just 12 hours in 2020. Attackers can easily purchase new email domains with just a few pennies, and a brand-new domain, with no malicious activity on its record, will pass most email security reputation checks with ease.
It’s a worrying trend for legacy security tools reliant on signatures and blacklisting. And this lifespan will continue to trend towards zero. In the near future, we can expect attackers to reach a stage where a new domain is created, a single targeted email is sent, and the attack infrastructure is then retired before the cycle repeats.
4. Phishing will become even more targeted
The overwhelming, rapid proliferation of ‘fearware’ this year has shown how effective targeted and topical phishing lures could be. The sheer availability of information online and across a plethora of social media platforms allows attackers to move from a ‘spray and pray’ approach to sending well-researched, tailored emails that have a considerably higher chance of succeeding. And as the technology becomes available to automate much of this reconnaissance, it is natural to assume attackers will take advantage of these tools.
5. Hackers will target identities rather than devices
For attackers going after businesses that have expanded remote working, targeted cloud services might be favorable to going after centralized, on-premise infrastructure. Email-borne fraudulent invoices could prove a quieter and more lucrative alternative for the money-minded cyber-criminal than ransomware. Successful impersonations of trusted suppliers frequently enable successful wire fraud attacks. And since these attacks involve ‘clean’ emails – containing no links or attachments – they usually skip past legacy security tools with ease.
The next wave of email attacks
Cyber-criminals continue to find new ways to skirt by the traditional, legacy-based email security tools commonly relied on today. Organizations must prepare now for the next wave of email attacks by turning to a new email security approach capable of neutralizing novel and sophisticated attacks that gateways miss.
Hundreds of organizations have adopted a self-learning approach that doesn’t rely on hard-coded rules and signatures, but uses AI to spot unusual patterns in email communications indicative of a threat. As attackers continue to innovate, having an adaptive email security technology that continuously reassesses emails in light of new evidence will be crucial for security teams.
Learn more about email security: https://www.darktrace.com/en/products/antigena-email/

Robin Shih, Product Director
The main reason ransomware can easily cause huge loss to many enterprises is that this kind of virus diffuses on its own. That is, it can spread across networks rapidly and attack those unprotected computers. Since there are numerous brands in the cyber security industry nowadays, theoretically, ransomware is supposed be solved easily. However, just like we need virus sample to make a vaccine, most equipment can find a solution only after it encounters attacks, and that is too late for defending ransomware. Thus, few has succeeded in real-time detection as well as blocking right after attacks happen, and the damage is often very serious.
N-Partner is a software developer in Taiwan and focuses on big data collection, effective process, and data analysis. With intelligent auto-learning algorithm, we can use the collected Flow data, like NetFlow or sFlow, to build a baseline. This way, when abnormal traffic shows up, the source device and IP will be found out in real time, and users can isolate them. The whole process is done by AI, and there is no need for manual threshold settings.
Since 12th May, 2017, the notorious virus, Wannacry, has thrived in the cyberspace. Our product, N-Reporter/N-Cloud, detected on the very same day that there was abnormal Flow bursting in lots if users’ environments by Flow analyzing. We did not know what kind of attack that was nor its name but was quite sure which computers had been invaded and were doing malicious diffusion. Our products also have port scanning function in IT management; as a result, besides sending alerts, we are able to locate those computers and IP addresses. Users can do collaborative defense with the switches and firewalls in the networks to block them and control the damage. This is the best example about how Flow analysis helps improve cyber security, and what's even better is that this solution can be built on a low budget.
Other than Flow mentioned above, N-Partner also applies the intelligent analysis function in log data. Here, we take DNS log as an example. DDoS attacks are still rampant around the world, and companies working on security has proposed cleaning to solve them. Nevertheless, there is no significant effect, because people usually do not have enough time to deal with them after being under an attack. We have done deep research about DDoS attacks against website services, and it turns out there are abnormal increase of DNS domain queries right before an attack. With intelligent analysis, we build a baseline for DNS domain query and do realtime comparison. Hence, we can provide early DDoS warning, and our users will have time deploying the defense system to defend their network.

In the past ten years or so, corporate IT has faced various hacking attacks from the outside. Internally, internal staff lacked awareness of the crisis of security, which led to internal security loopholes. How should enterprises deal with the endless stream of security risks?
First of all, information security awareness needs to start with comprehensive training and education, so that employees are always mindful of security risks, and then it will be strengthened through the use of fully functional and continuously updated technical equipment.
According to the market's information security needs, most NAC (Network Access Control) products can meet the 80% coverage rate of the functions required by the enterprise, but after all, the types of industries are different. The information security functions required by each company are Difference. Therefore, the 20% coverage rate that cannot achieve the functions required by the enterprise is the difference in the demand for information security functions between industries.
Faced with the current industry NAC product functions in various industries, it is nothing but IP (IPv4 and IPv6) distribution and blocking management, Switch device management, terminal computer virus code and system patch management, end user AD management, and visitor management and many more. PIXIS Technology's PIXIS DSI products meet the basic functions required by the industry, are more committed to technical advancement, have obtained multiple patent certifications, and provide special features based on customers' actual needs, such as supporting multiple sets of antivirus software and their It is very practical for enterprises to update, block private APs from duplicating legitimate MACs, one IP with two MACs and one MAC with two IPs, automatically detect all devices, and display a topology map of the traffic used by each device. Required features.
The reason why PIXIS Technology's PIXIS DSI can more closely meet the needs of industrial functions is that PIXIS Technology's team has customer experience management in addition to the accumulated experience. Handle and solve the customer's worry on information security at the end of the operation. PIXIS Technology's team is also young, so externally, facing various evolving security issues that are rapidly evolving, it can respond as an amoeba and provide customers Fast and accurate customized services, in-house, actively training internal staff to improve professional skills, can more flexibly face the needs of various industries.
With the rapid development of IoT and 5G networks, the IPv6 network world is coming sooner. PIXIS Technology's PIXIS DSI system has the integrity, ease of use, and scalability, which can help administrators painlessly implement IPv6 or dual-protocol networks.

Following enterprise's digital transformation, enterprise's IT environment infrastructure has gradually loosen itself from the traditional bound, and enter the virtualization or even cloud based micro service architecture. Quickly satisfy enterprise's need for flexable resource deployment.
On such dynamic infrastructure, if still using old method or even deploy the architecture that's initially designed for traditional software and hardware management, it'd become very easy to encounter many obstructions and difficulties, also it'd not be able to provide complete system and service protection.
Because of the covid-19 in Taiwan in these years, it has resulted in serious lack of resource and workforce, and also made significant change on the work style. And these changes have made the use of modern digital services become even more widely acceptable. At the same time, it also attracted the attention of hacker organizations even more because of enterprise's wide deployment of these applications. The attacks from hacker organizations are often hard to trace, for example the ransomware's encryption attrack on important systems or files, has resulted in ransom threat to enterprise.
It doesn't matter whether the ransom has been paid, enterprise must have a counter-strike method to deal with these affected systems or files. So as to protect its important backup file during the attack, and also at the same time be able to ensure the critical systems can be recovered and started up right away during the attack, to shorten the possible downtime.
Using Veeam solutions, enterprise can use the most cost effective method to lock its critical backup data, enterprise can also recover damaged system via the use of instant system recovery function. At the same time, enterprise can also trigger automatic virus scanning during the system recovery process to remove any possible virus attack.

DevOps is a common software development model in recent years. The spirit of DevOps is to integrate development and operation (DevOps). However, with the rise of security information security risks, the security requirements for software development quality are stricter. How to integrate the security into the software development culture is a challenge for DevOps development process. By adding security into the CI (Continuous Integration) /CD (Continuous Deployment) pipeline, the developers can identify the problems more efficiently, and improve the quality of software products.
III DevOps tool solution based on open source software is developed by Institute for Information Industry to integrate information security into the DevOps process. The tool also applies the open source software license terms.
The purpose is to integrate information security testing tools into the CI/CD development process. During the software development process, after the developer uploads the source code, the testing can be initiated automatically after the developer uploads the source code, including information security testing such as Source Code Analysis and Vulnerability Assessment
The testing result can be generated automatically to the platform, and this will allow users to quickly find out the quality and current software development status.
And it can automatically return the test results to the platform, allowing users to quickly understand the quality and status of the current software development, so that developers can view related problems at the early stage of the software, avoiding past testing modes, which are only found in the final testing stage of the product Problems, but thought it was too late, or it took a lot of material and manpower to improve the problem.
Function and features:
1. Include both software engineering, and CI/CD project management requirements: integrate Gitlab, jenkins, Rancher, Redmine, Postman... and many open source solutions.
2. The platform provides multi-role functions: there are three main roles, including system administrators, project managers, and developers. And the platform provides management interfaces and tools to each role.
3. Switch between the open source tools and III DevOps user interface: users can use the interface provided by the III DevOps platform or open source tools such as Gitlab, Redmine, etc.
4. Containerization: system components and systems are deployed on Kubernetes, which can support Horizontal Pod Autoscaler (HPA).
5. Support multi-environment deployment: provide optional fast deployment services for different development languages, frameworks, and execution environments.
6. Flexible value-added service: The platform provides a system interface with external tools, such as information security inspection tools (Checkmarx, CxSAST, Fortify, WebInspect, SonarQube…etc.).
7. Strengthen DevOps automation: According to the flexible value-added services, the test results can be converted into issue to developers automatically in continuous DevOps cycle.
In Cybersec 2021, the integrated III-DevOps tools, fault tolerance techniques, and multi-cloud management technology will be exhibited at booth S10 by Institute for Information Industry.
For more information please visit www.iiidevops.org

Jay Jang/Consulting Team Manager
While traditional WAFs depend on high-maintenance signature updates for low-accuracy pattern-matching, WAPPLES uses a logic-based detection engine called COCEP™ (Contents Classification and Evaluation Processing).
Utilizing 34 pre-configured detection rules, modified and even unknown attacks are categorized and blocked heuristically and semantically. This proprietary technology allows WAPPLES to deliver superior security with industry-leading accuracy and low false positive rates under various network environments. Maintaining high stability and performance, WAPPLES’ ease of deployment and low operational workload was recognized by Gartner as what made the WAF a popular choice for surveyed clients.
Through the analysis of an attack’s characteristics, WAPPLES is able to identify attacks that utilize new patterns of exploit that often bypass typical WAFs utilizing signature-based detection engines.
Besides blocking basic web attacks, WAPPLES is deployed to effectively guard against sensitive data leakage, block malicious web access and prevent website defacement in this era of intensified attacks.
Powered by an intelligent detection engine, WAPPLES is capable of combating the newest threats, including attacks often utilized in Advanced Persistent Threats (APT) launched by malicious agents to obtain data assets of governments and enterprises or for terrorism or political gains.
As a market share leader in Asia-Pacific for four consecutive years, WAPPLES is the web application firewall (WAF) of choice for enterprises, governments, and NGOs worldwide.

Since L7 was founded at Hsinchu Science-Based Industrial Park in 2002, L7 focus in network security. In this field, very rare local vendors can provide security products that can fit in large core networks. Most local vendors focus on hackers, SOC, email, EDR because core network is too big and affect too many services. Products installed at core networks are not easy to be stable enough to interconnect with Cisco / Fortinet / PaloAlto.
For example, the cloud data center in Department of Internal Affairs has hundreds of services within a portal. Outside visitors need to pass (1) L7 server load balancer "InstantBalance" to be redirected to (2) L7 reverse proxy "InstantWAF" to do SSL decryption and WAF filtering, and then to dedicate virtual machines operated by internal divisions, which is also load balanced by (3) L7's virtual load balancer "InstantBalance" to reach the actual server. For outgoing traffic, internal users must pass (A) L7's forward proxy server "InstantCheck" to filter behaviors and go to (B)L7's application bandwidth manager to quarantee / limit bandwidth, and pass through (C)InstantGuard subscribed service which integrate more than 8 threat intelligence to stop zombie PCs from connection back to C&C servers. L7 boxes sit among US security products and are gradually exposed to the public, and are becoming more and more important role for the national defense line.
In above (1), (2), (3), (A), (B), (C) processes, core traffic usually reach multi-gigabit per second. 10G network interfaces are also very common. To keep the system stable with high availability and fault-tolerant hardware bypass, L7 must fast respond to the system crash when we are under attack. This is the essential ability to have in core networks. Aside from that, SSL decryption is also important to catch crime and record the trace within encrypted channels.
From L7's cyber insight, high-speed recognition of tunnelled criminal behaviors is essential, just like catching people in fever from a lot of crowd, and is a must to play the role in the national defense line.

One of the IT trends in 2021 is that with the maturation of the cloud and the growth of edge networking with its myriad endpoints – all accelerated by the explosion of IoT – how security is defined and implemented is now becoming part of the network architecture, and not some bolted-on component of the enterprise IT environment.
Actually we enter 2021 in a very different place from where we were at the start of 2020. In 2020, remote work and distributed computing have proven successful for many job functions, and work-from-home will continue well into the future. Meanwhile, State-sponsored cyberattacks are at an all-time high and it’s imperative to protect users, devices, and data wherever they are located. IT needs complete visibility into and control over its networks. IT will accelerate security measures, including strong access controls, AI-driven cybersecurity, and network modernization and additional segmentation to protect high-value data. That necessitates an even greater focus on Zero Trust security.
The concept of Zero Trust is nothing new and has been around for almost a decade. Zero Trust, at its core, is a security policy for your organization that removes traditional boundaries such as firewalls, routers and switches from being the only factor used to determine if a device is trusted or not. With this model, you are no longer trusting devices just because they are connected to your network. Zero Trust has emerged as an effective model to better address the changing security requirements for the modern enterprise by assuming that all users, devices, servers, and network segments are inherently insecure and potentially hostile.
In practice, building a Zero Trust architecture may be easier if done from greenfield. It does allow brownfield organizations to adopt the principles and add additional layers to their existing security models. Zero Trust varies significantly depending on which domain of security is being considered. Although application-level controls have been a focal point within Zero Trust, a comprehensive strategy must also encompass network security and the growing number of connected devices, including the work from home environment.
Aruba has long been a leader in secure networking solutions. Zero Trust network architecture solutions will remain a core piece of effective security with traditional IT workloads moving out of the Edge into either the cloud or SaaS environment. The vacuum left behind is eventually going to be replaced by OT/IoT specific workloads at the Edge. Furthermore, with the implementation of 5G, the networking architecture must contend with multi-access edge compute (MEC) workloads – both private and public – all the more necessitating dynamic approaches to security policies beyond the user-centric workflows that Zero Trust is primarily optimized for today.
Aruba Zero Trust Security ensures that the same controls can be applied to your campus or branch network to help you achieve the following goals:
1. See what's connected to your network:
With the increased adoption of IoT, full spectrum visibility of all devices and users on the network has become an increasingly challenging task. Without visibility, critical security controls that support a Zero Trust model are difficult to apply. Automation, AI-based machine learning, and the ability to quickly identify device types is critical. Aruba ClearPass Device Insight uses a combination of active and passive discovery and profiling techniques to detect the full spectrum of devices connected or attempting to connect to the network. This includes common user-based devices such as a laptops and tablets. Where it differs from traditional tools is its ability to see the increasingly diverse set of IoT devices that have become increasingly pervasive on today’s networks.
2. Use identity and roles to enable access to IT resources:
Once visibility is in place, applying Zero Trust best practices related to “Least Access” and micro segmentation are critical next steps. This means using the best authentication method possible for each endpoint on the network (i.e. full 802.1X and multi-factor authentication for user devices) and applying an access control policy that only authorizes access to resources that are absolutely necessary for that device or user.
Aruba ClearPass Policy Manager enables the creation of role-based access policies that enable IT and security teams to operationalize these best practices using a single role and associated access privileges that are applied anywhere on the network – wired or wireless infrastructure, in branch or on campus. Once profiled, devices are automatically assigned the proper access control policy and segmented from other devices via Aruba’s Dynamic Segmentation capabilities. Enforcement is provided by Aruba’s Policy Enforcement Firewall (PEF), a full application firewall that is embedded in Aruba network infrastructure. Aruba infrastructure also utilizes the most secure encryption protocols such as the WPA3 standard over wireless network connections.
3. Dynamically change access privileges based on real-time threat data:
With over 150 integrations made up of best-of-breed security solutions that include Security Operations and Response (SOAR) tool sets, ClearPass Policy Manager is able to dynamically enforce access based on real-time threat telemetry coming from multiple sources. Policies can be created to make real-time access control decisions based on alerts coming from Next-Gen Firewalls (NGFWs), Security Information and Event Management (SIEM) tools, and many other sources. ClearPass actions are fully configurable from limiting access (i.e. Internet only) to fully removing a device
from the network for remediation.
Through the ClearPass ecosystem, customers can also easily incorporate other
solutions to meet Zero Trust requirements related to contextual information and other security telemetry. This means ClearPass can integrate with a wide variety of solutions such as Endpoint Security tools to make more intelligent access control decisions based on a device’s posture. Access control policies can also be changed based on which type of device is being used, where the user is connecting from, and other context-based criteria.
Aruba’s threat defense capabilities defend against a myriad of threats, including phishing, denial of service (DoS), and increasingly widespread ransomware attacks. Aruba 9000 SD-WAN gateways perform identity-based intrusion detection and prevention (IDS/IPS), working together with Aruba Central, ClearPass Policy Manager, and the Policy Enforcement Firewall. Identity-based IDS/IPS performs signature- and pattern-based traffic inspection on both the branch office LAN (east-west) traffic as well as the SD-WAN (north-south) traffic flowing through the gateway to deliver embedded branch network security. An advanced security dashboard within Aruba Central provides IT teams with network-wide visibility, multi-dimensional threat metrics, threat intelligence data, as well as correlation and incident management. Threat events are sent to SIEM systems and ClearPass for remediation.
Work from home, digital transformation, and IoT require innovative security strategies. In Summary, Aruba Zero Trust Security in response to such a rapidly changing situation.
The benefits of Aruba Zero Trust Security
• Adopt holistic security
There are many definitions of Zero Trust. Only Aruba provides the key elements for implementation: Complete visibility, authentication, policy-based access authorization, and attack detection and response.
• Eliminate VLAN sprawl
Zero Trust with Dynamic Segmentation leverages user and device identity to set role-based IT access permissions enforced by the network infrastructure–independent of how or where the connection is made.
• Integrate security ecosystems
Aruba ClearPass Policy Manager integrates with 150+ third-party security solutions. It updates those solutions when users and devices access the networks, automatically changing access rights to respond to issues detected by our partners.
More Information:https://www.arubanetworks.com/zh-hant/solutions/zero-trust-security/
Aruba Zero Trust video:https://www.youtube.com/watch?v=EVXCizp83aI

Combining technology, experience, and localized intelligence to launch NEITHInsight and NEITHSeeker
As cyber threats have increased every day, the issue of cyber security is a national security issue that must be dealt with while pervasive ransomware has terrorized enterprises and the government. In addition to well-known companies such as Formosa Plastics and China Petroleum Corporation being attacked by ransomware, it has also been reported that many well-known high-tech companies have also come under attack in 2020. Not only has this severely impacted the normal operations of these companies, but the attacks have also severely impacted their reputation. Even though most companies have established security mechanisms, the security appliance has also picked up the abnormal behavior of the ransomware. While warning messages are continuously being sent, information security personnel could not find where the ransomware was hiding. This is because companies lack a set of Indicators of Compromise (IOC) platform to assist their search and the information security personnel have insufficient professional and technical capabilities, which eventually lead to the unfortunate attacks carried out by ransomware.
Because of this, NEITHNET has gathered plenty of cyber security experts and officially announced the launch of NEITHInsight, an IOC platform that integrates global and Taiwan’s local intelligence; NEITHSeeker, a Managed Detection and Response (MDR) service to help companies deal with cyber security incidents. The NEITHNET cyber security team has been involved in tracking the different types of hacker attacks and past intelligence about them. The team mainly focuses on the research of cyber threats and the R&D of technology. They are particularly good at analyzing large-scale network DDoS traffic and connection attacks, DPI network behavior packet analysis, and the behavior analysis of malware network attacks.
NEITHNET CEO ART Lin said that ransomware has terrified people as they began lurking in companies for months or even longer, silently figuring out the network structure and collect data to eventually attack at a preset time. Most cyber security devices will detect the ransomware's abnormal behavior and send out warnings during the lurking period. However, there still isn’t enough information from the warnings to help information security personnel to find out the hidden location of the ransomware. As a result, an IOC platform would help cyber security personnel find the files infected by the ransomware in the shortest amount of time, which is why NEITHNET launched NEITHInsight.
There are many IOC platforms on the market, but most of the intelligence is global. They lack supportive intelligence exclusive to Taiwan, which weakens the effectiveness of these platforms. In addition to retaining global intelligence, NEITHInsight also integrates a large amount of localized intelligence acquired from the Taiwanese network environment to effectively assist information security personnel in identifying attacks, shortening the time required to detect ransomware or malicious threats. Secondly, NEITHInsight's intelligence collection scope is quite broad. In addition to intelligence from external attacks, NEITHInsight also includes intelligence on ransomware and malware intrusion that can be distributed and reported back within the company, which makes it even more precise and naturally trustworthy.
It is worth mentioning that NEITHNET has also established a world-class cyber security laboratory (NEITHCyber Security Lab), which can verify the intelligence’s validity and even conduct back-testing analysis. Meanwhile, the Lab can also simulate real network environments to accurately understand malware attack patterns and their subsequent impact.
CEO ART Lin pointed out that in view of the insufficient cyber security talent around the world, most companies face the dilemma of having a large amount of log regarding these incidents and not having enough manpower to deal with them. That is why the company launched NEITHSeeker, which will hopefully help companies handle cyber security threats as fast as possible. NEITHSeeker automatically collects and analyzes the intelligence generated by the company's internal network and cyber security equipment, and can respond immediately when an abnormality is detected to control cyber security threats down to a minimum level and ensure the security of the company's digital assets. Compared with the MDR services of other companies, we are superior in terms of professional capabilities and experience. The combination with NEITHInsight's localized intelligence allows us to provide more effective cyber security services.
In face of unpredictable and attacks ever-changing cyber world , NEITHNET will focus on promoting NEITHInsight and NEITHSeeker in 2021, let more companies understand the importance of IOC platforms and MDR services and establish effective cyber security mechanisms to combat the ubiquitous threats.
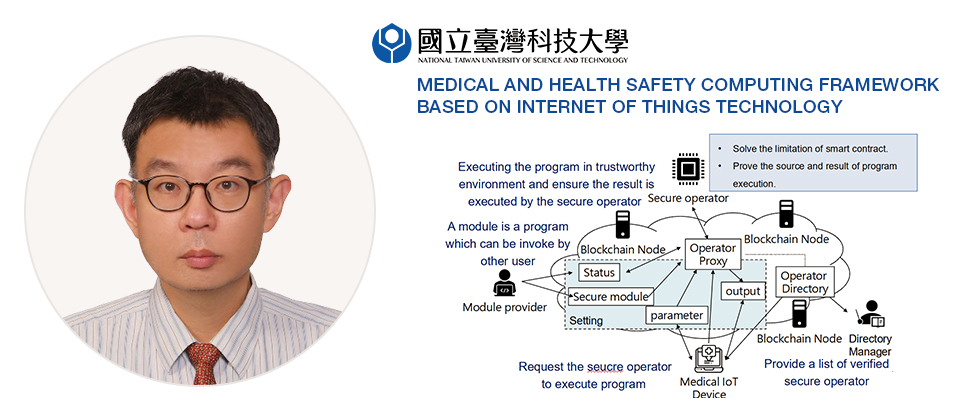
Shi-Cho Cha/Professor, Department of Information Management, National Taiwan University of Science and TechnologyChief, Taiwan Information Security Center, National Taiwan University of Science and Technology
With the rise of “Internet of Things, more and more medical products provide internet service to upload and analyze the users’body measurement value in order to help users to let them know their physical health. However, it is difficult for users to distinguish whether the device provider store and process their data appropriately or not.
The Secure Computation Framework is consist of secure operator and smart contract. The hardware secure module provides a trustworthy execution environment to protect the confidentiality and privacy of users’data and write the result back to blockchain.
Through integrating the Secure Computation Framework, to upload the value received from IoT devices to blockchain and trigger the secure operator. When meeting the condition, the secure operator would trigger the webhook which would notify the specific server. Moreover, the data is encrypted so the user and secure operator who share the data encryption key previously can retrieve the data.

JRSYS is a well-known mobile security and cloud security Taiwanese company with 100% independent innovated R&D in Taiwan. An international security team based on Taiwan and already have international customers. In addition to possessing nearly 20 mobile information security-related invention patents in Taiwan, China and The State. Jrsys has won a number of international information security championship awards, including but not limited the APICTA Award champion of the Asia Pacific Information Security Contest.
In recent years, there have been frequent hacking incidents, and many well-known companies have been shot down accordingly. In addition to affecting business operations, they have also caused the leakage of personal information of customers and consumers. The purpose of establishing information security management is to reduce various business risks and avoid major losses or unbearable impacts caused by sudden information security incidents. Therefore, in accordance with the requirements of the international information security standards ISO 27001 (ISMS), ISO 27701 (PIMS), ISO 22301 (BCMS), and IEC 62443 (CSMS), the IT/OC/CT/BC security protection software framework that may meet with the needs of modern business requirements.
The standard of JRSYS’ information security protection is to adopt international information security standards, emphasizing CIA (confidentiality, integrity and availability). Factory automation information security is based on the international IEC 62443 standard, emphasizing that AIC sequence and Availability should be put first, because on the operation level, it is not possible to stop the machine while in processing.
The integrated information security of JRSYS production information includes the diagnosis, consultation and necessary solution introduction. In addition, production line information security, supply chain information security, and identity authentication information security are also indispensable and important links in the overall industrial control information security field.
The industrial automation information security provided by JRSYS includes the access control that corresponds to IEC.62443-2-1 and all enterprises face every day, including: account management, authentication management, authorization management, etc. According to these basic information security policies and adopted products, then decide other peripheral hardware and software accordingly.
The recommended approach for the B2B protection mechanism of the OT Security starts with the pain point of the industry.
The current OT Security pain points include:
- Worry about the Internet being attacked by hackers.
- There are many networked machines and system hubs, and the password must be highly complex, each must be different, and it must be replaced regularly, which is too difficult to remember and manage.
- The company's B2B supplier employees turn-over and the passwords are transferred to the successors, but the company itself does not know and cannot control it. The worry is that the turnover personnel could illegally log in to the company with the same account and password to obtain secret information.
- The company was invaded by hackers, causing the payment of goods to be remitted to the hacker's instead, and there have been endless incidents that harmed the company and various suppliers and vendors, with losses of tens of millions to billions.
- The important production parameters and formula ratio of the machine are important intellectual property rights of the company. How to protect?
- How to manage and save a large number of documents with suppliers: inquiry for quotation, contract, warehousing acceptance form, shipping order and various documents in the production process?
Based on the above industry pain points, the solutions proposed by JRSYS include:
- The company must have a firewall to establish a DMZ demilitarized zone to protect external connections.
- Through the highest authority management system to complete important password management of servers, databases and machines.
- Using 2FA authentication to simply and effectively control and solve the possible risks caused by the turnover of supplier employees.
- Digital paperless electronic documents must be electronically signed to confirm the correctness and authenticity of the documents, avoid tampering and forgery, and then store them through electronic documents to reduce the cost of data searching and storage.
- In the COVID-19 post-epidemic era, it is a more convenient, fast and safe solution to exchange documents with suppliers through online sign-off and eMail but protected by IT/OT/CT security.

By any metric, 2020 was a busy year for cybercriminals. A combination of COVID-related disruption and increasingly sophisticated threats saw more organisations fall victim to common cyber attacks.
Proofpoint’s 2021 State of the Phish report found that 57% of organisations suffered a successful phishing attack last year. The consequences were far-reaching and damaging. Almost two-thirds lost data as a result, with half experiencing account or credential compromise.
Another old foe, ransomware, remained a scourge for organisations in 2020. While the prevalence of attacks was similar to previous years, more organisations are playing ball and handing over ransoms. Unfortunately, with mixed results.
Of the two-thirds of organisations that suffered a ransomware attack last year, half opted to pay the ransom. Just 60% regained access to their data after the first payment. Others were met with additional ransom demands or no response at all.
That old tricks like phishing and ransomware are still fit for purpose should worry cybersecurity teams. While the fall out of the pandemic certainly impacted last year’s cyber attack success rates, it was just one part of the problem.
What’s arguably more concerning is the increasingly convincing and focused nature of modern threats. Cybercriminals are now actively targeting your people rather than your networks or infrastructure.
And while technical protections continue to advance at pace, user awareness is still not up to speed. For as long as this remains the case, organisations are effectively bolting the front door while leaving the back door unlocked.
Closing the awareness gap
User awareness is the most critical tool in your cyber defence arsenal, and as important as any technical protection or control. Despite this, it is rarely afforded the same level of focus or resource.
Almost 100% of organisations have a security training programme in place. However, a look behind that statistic reveals the true story.
For almost half of those organisations, security awareness training takes place no more than four times per year. And even then, the majority spend fewer than two hours on the subject. To compound the issue, only half carry out company-wide training, with just 60% delivering formal training sessions in-person or virtually.
This lack of comprehensive training is clearly reflected in user awareness. With high profile attacks never far from the headlines, it will surprise many to learn that just 33% of users correctly understand the definition of ransomware. An equally concerning 65% and 63% understand malware and phishing, respectively.
While this may seem unbelievable to cybersecurity professionals, it highlights the gulf between recognition and understanding.
Your users may be aware of household and globally recognised brands that have fallen victim to phishing or ransomware attacks. But that doesn’t mean they understand the mechanics of the threat. And it certainly doesn’t indicate an understanding of their role in defending against it.
To close this knowledge gap, security awareness programmes must go beyond the basics of common threats, educating users on their cybersecurity responsibilities.
Identifying your Very Attacked People
To deliver the right education to the right people, you must first identify who in your organisation is most at risk. At Proofpoint, we call those users your Very Attacked People (VAPs).
You should let go of any preconceptions you may have when undertaking this research. Your VAPs can sit in any role at any level of your organisation. While attacks on VIPs such as board members may be more lucrative, attackers often target those lower down the hierarchy. VAPs also vary significantly between organisations and across industries.
In a recent example, Proofpoint observed that the top 20 VAPs of a large healthcare organisation were also VIPs. On the contrary, only one VIP was targeted during the same three-month span at a financial organisation.
And this is just a snapshot. Much like security awareness training, identifying VAPs is not a one-time activity. They will always change over time, with users dropping in and out of the most targeted list from month to month.
Once your VAPs are identified, you can assess their security awareness levels. With this information, you can build tailored training programmes. Programmes that deliver education in the context of individual risk profiles and focus on critical gaps in user knowledge.
This is People-Centric Cybersecurity. And it is often the only thing standing between cybercriminals and your data, networks, and systems.
Building a people-centric cyber defence
Cybercriminals are steadfast in their commitment to attacking your organisation. If you fail to show the same commitment to defending it, the outcome is all but predetermined.
Technical controls, processes, and best practices are not enough on their own. User behaviour is the biggest risk factor for the modern organisation. And changing that behaviour is paramount to a robust cyber defence.
This is only possible by creating a culture in which cybersecurity is not just a concern for IT. It is everyone’s responsibility. This culture is nurtured through regular, in-context awareness training. Training that is tailored to your users and an ever-evolving threat landscape.
You are not just training users to pass a test. You are training them to defend your organisation. Your security awareness training programme must reflect that. It should go beyond dictionary definitions and simulated attacks. It must focus on behaviour and how that behaviour increases risk.
When users understand the link between reusing a password and a data breach or clicking a link from an unknown sender and ransomware, behaviour changes: 80% of organisations say security awareness training has reduced susceptibility to cyber attacks.
Cybersecurity is no longer just a technical discipline. In the age of people focused attacks, knowledge and awareness are key. The more your users know, the safer your organisation.

In the past few years, many clients have been suffering from the attacks of targeted ransomware. Thus, QNAP, as a leading NAS company, aims to provide a comprehensive data protection solution to help our customers to avoid potential risks and hazards. Historically, ransomware attacks have not been classified as new malicious attacks since the massive Wannacry outbreak in 2017. Techniques of targeted attacks were also seen in many national-sponsored attacks. However, more than half of the technology manufacturers, health and welfare sectors, and public sectors are harmed by the newly targeted ransomware attacks last year, 2020, when the COVID-19 strikes.
Why corporations have been attacked by targeted ransomware so easily and resulted in encrypting files in most employee’s computers, factories’ computers, and servers? As a result, we will discuss the defense strategies and uncover the dilemma of choosing the most suitable cybersecurity solution for end-customers.
First, traditional cybersecurity solutions. Traditional cybersecurity companies provide the first defense layer which is like a city wall against known malicious cyber-attacks and malware. However, in the recent 10 years, targeted attacks and unknown malware has blossomed, and most enterprises have come to realize that there is no cybersecurity solution that has a 100% detection rate, and severe outcomes will inevitably happen even if there’s only 1% of the computers are compromised because of the difficulties of detecting lateral movements. Therefore, a lot of enterprises have paid a painful price to the cyber incidents.
Furthermore, QNAP NAS is located in the innermost layer of the intranet. Therefore, it will mean the final exfiltration stage of the attack if the attacker reaches QNAP NAS. That is to say, it is the last attacking phrase in the kill-chain. Therefore, defense-in-depth and network detection and response are the resolutions that are recently promoted by cybersecurity providers. However, to be honest, most customers still suffered from the hard-core targeted ransomware attacks and interrupted recovery in the past two years and they have completely relied on the backup and restoration solution that QNAP has been providing.
We contemplated why there isn’t a more effective way to respond to the targeted ransomware attacks? There are two reasons for the above, the high total costs of the implementation and the complexibility of the cybersecurity solution. For one, companies will need to spend millions of or even tens of millions of bucks on the solution from NDR cybersecurity providers. NDR solution deploys aside the core switch and has full-scanning on the pre-configured channel or protocol of traffic which is much less than all traffic due to the inability to scan the massive traffic from the core switch. Furthermore, Enterprises are facing the challenges to analyze all results from these detections as actionable insights since most of them lack skilled security experts. As of the results, decision-makers especially executives are typically not to make the decisions along with these cybersecurity solutions since it is practically not effective.
We, QNAP, would like to propose a new and innovative approach for the protection of targeted ransomware which we focus on effective and early detection of lateral movement stage. With adaptive screening, early detection and response, and completed threats analysis, the risk of attacks can be managed and controlled in the smallest amount of computers. Let’s picture this as the war of pandemic preventions. Typically, the center of the disease will construct the first layer of detection in the airports. However, this can’t prevent or filter the patients without symptoms and, when patients are validated with full medical checks in the hospital, an outbreak in the community or city might have happened since the patients have already spread the virus outside for a while. Therefore, if we can deploy a station in each community with accurate and quick screening, giving the confirmed patients early treatments and quarantine. We can probably enhance the chance of preventing the outbreak while also saving resources on recovery.
Last but not least, apart from the ADRA NDR Series, QNAP also provides other advanced data protection features, such as snapshots, virtualization applications, WORM, and QuObjects for customers to enact a more precise, effective, and complete cybersecurity solution. We are pleased to give you more information about our newly-released product, ADRA NDR adaptive screening and cybersecurity switch in CYBERSEC 2021. Stay tuned!

Ransomware infection can be roughly divided into three stages: entry, spread, and encryption. Since the development of ransomware, encryption methods and complexity continue to evolve. Once enterprise data is encrypted by ransomware, cracking the key becomes an impractical method. The only way to save the encrypted data is to back up the data or pay a high ransom. The fundamental way to solve the problem is to catch and remove the ransomware at the initial stage of infection, which is the stage of "entering" and "spreading", in order to effectively avoid the risk.
Before distributing ransomware, hackers first need to enter the corporate intranet. Hackers usually scan each IP to attack until they find a device with security vulnerabilities. After breaking through the intranet, they can control the terminal device, using it as a jump server, and then gradually obtain higher-privileged accounts, invade the enterprise AD, break into the Domain controller, so that the ransomware can be transplanted horizontally, spreading, and infecting the entire local network. Therefore, to block ransomware from the internet, you can use the following methods to make it less possible for hackers to take advantage:
1. Turn off the remote desktop function
The Remote Desktop Protocol (RDP) is a proprietary protocol developed by Microsoft that allows users to remotely connect to a computer with other devices. Hackers can use the same channel to gain access to the computer by using leaked RDP certificates or simply cracking the targeted computer. When the hacker enters the computer, he can do anything, including changing the password, installing malicious programs, burying backdoor programs, etc. Most companies do not have comprehensive policies on passwords, making the password strength insufficient, and hackers can easily enter the network and cause damage. Therefore, RDP has become one of the main channels for hackers to invade. Turning off RDP will bring a certain degree of inconvenience, but it can be very effective in reducing the chance of hacking.
2. Comprehensive IT Asset Management
Security vulnerabilities in software and Windows OS are also the main ways for hackers to invade the intranet. In 2017, WannaCry, a well-known ransomware, raged 150 countries, causing more than $4 billion dollars losses, through a Windows OS vulnerability which Microsoft had released two months ago. Therefore, it is necessary to ensure that all devices in the enterprise are updated to the OS version in the first time, no pirated software is used and all software is updated to the latest version.
3. Minimize account permissions
In order to prevent hackers from installing malicious software to the intranet, the permissions of the local account should be minimized and the AD account should be managed to avoid giving unnecessary permissions.
4. Use of anti-virus software and update of virus signature
Although it is difficult to detect ransomware through anti-virus software, malicious programs such as backdoor programs can be intercepted and removed by anti-virus software. Therefore, the anti-virus software should be maintained at the latest version and the virus signature provided by it should be kept up to date in order to completely prevent hackers from gaining access to the intranet through malicious programs.
5. Establish a good information security awareness
Hackers often use fake websites and phishing emails to induce employees to download malicious programs to attack the intranet. The behavior of employees is the most difficult factor to control. Poor usage habits and security awareness can easily cause intranet infringement. Therefore, establishing a sound information security education system and cultivating employees' good information security awareness is also a link that needs attention.
How UPAS prevents ransomware
UPAS specialized in intranet management. We provide many measures to effectively block ransomware from the internet. UPAS adopt zero-trust architecture to minimize the impact of security vulnerabilities, and can instantly detect anomalies in multiple links when hackers launch targeted infiltrations.

Spirent provides a variety of comprehensive managed testing services, delivered by certified, seasoned professionals. We can proactively identifying vulnerabilities and mitigating risks.
Red Teaming is always objective-driven and simulates a real-world scenario. Uses various physical, electronic, and social engineering techniques to try to exploit your personnel and any physical weaknesses in order to gain access to the premises.
Purple Team Assessments solution safely generates hyper-realistic emulated security assessment traffic on the exact services you are protecting. It emulates attack propagation and pivoting behavior so you get an accurate assessment of complex security countermeasures.

Looking back at the year 2020, the world has been enveloped in troubles related to the Coronavirus, which continues to change the way people work and live. In the past, companies were accustomed with traditional corporate routines like face-to-face meetings, interactive customer contacts or interviews with corporate staff, now it has been significantly replaced by remote interactive meetings; including contract signing, cash flow, and sensitive data exchange, etc… Online discussions with internal and external stakeholders have become the new norm; while these are observed trends, it is easy to imagine that the internet network, financial network, and transmission of sensitive information would lead to increased vulnerability to cybersecurity issues. With the heightened information flow, ensuring the adequacy of network security mechanisms and employee information security are important keys to company survival.
Establishing a SYSTEX cybersecurity research and development team to create in-house solutions for corporate customer success
In addition to being the agent of many domestic and foreign cyber security products, SYSTEX Corporation also cooperates or engages in technology transfer with information security units in related industries, government and academia, such as the Institute for Information Industry, Industrial Technology Research Institute, National Center for High-Performance Computing. A sophisticated cyber security solution is built through SYSTEX Corp.’s five core products: RedAlert, Cyber Center, Monitoring and Operation Center (MOC), SYSTEX Email Security Cloud (SESC), Human Error Insight System (HEIS).
SYSTEX Corp.’s “RedAlert” is a product of collaboration with the National Center for High-Performance Computing that is built on the Cyber Defense Exercise Cloud Platform. It simulates red and blue teams in cyberspace, where the red team plays the attacker role and the blue team comprises the organization/enterprise in test. The RedAlert operates as an SaaS which aids in strengthening cybersecurity through hands on exercises and simulations on cyber attack remediation.
Cyber Center, a product of SYSTEX Corp., employs advanced big data and artificial intelligence technologies to effectively and accurately analyze cyber cases, providing businesses a clear picture of their cyber threat. Its Security Operation Center (SOC) integrates cybersecurity assessment, vulnerability assessment, social engineering simulation, red-teaming, and internationally recognized training programs, setting it apart as the leading one-stop service provider in cybersecurity.
SYSTEX Corp.’s Monitoring and Operation Center (MOC) is a real-time monitoring solution designed for various situations and fields, including long-term cybersecurity threat tracking. The system is backed by professional constants 24/7, providing timely services from the Taipei and New Taipei cities to protect enterprise property, control data flow, and flag threats when necessary.
The SYSTEX Email Security Cloud was designed on a user-initiative, to address the most common cybersecurity threats faced by Taiwanese firms. It integrates local and international benchmark products, and offers a subscription model to access an email security cloud. Furthermore, it contains diverse protection and customizable application models incorporating AI techniques into semantic analysis protection engine, malware, APT, URL, etc… , making it the leading Next Generation Email Security Cloud Platform.
Emails remain as one of the crucial communication tools of an enterprise, but have also become a prevalent route for cyber attacks. According to statistics, as high as 92% of suspicious emails contain malicious links that traditional “spam mail” cannot detect.
Over the course of history, the element of “humans” has been the most vulnerable and most difficult to manage. According to Gartner’s Key Strategic Technologies Report of 2021, topping the list of 9 strategies is the idea of Internet of Behaviors (IoB). Since the hit of the coronavirus, one can imagine the diversified internet behaviors and the resulting reliance on internet connectivity. We may forecast that a growing importance of data and analysis will be seen, elevating the vitality of data governance and cybersecurity. SYSTEX Corp.’s Human Error Insight System (HEIS) addresses these trends and offers a solution for security awareness training of the regular employee. The goal of the program is to fortify the enterprise’s cyber defense line through targeted and customized simulation training that collectively increases employee security awareness.
Connecting with the cybersecurity startup space, cultivating hands on cybersecurity talent
In the face of constantly changing cyber attacks, corporations must abandon the “cybersecurity hardware purchasing” myth, instead focus efforts on the human factor. Cybersecurity hardware and softwares are merely supporting functions, humans are the true missing link to an effective cyber defense program. All employees must be equipped with security awareness in their day-to-day activities, and security personnel must also do their part to manage relevant programs in order for the corporate defense program to succeed.
A huge challenge in the industry has been the constant lack of qualified cybersecurity personnel. Cybersecurity is an extension of national security, which is the reason why the Legislative Yuan has approved a NTD 809 Million budget to build a national-level cybersecurity institute for professional training. The target is to become APAC’s revered cybersecurity talent and technical pool within 2 years.
We believe that although Taiwan has numerous excellent engineers, there is a lack of qualified cybersecurity personnel. Thus, SYSTEX Corp. aggressively invested in cybersecurity talent training and upgrading from the aspects of: R&D expertise, service expertise, and consultant expertise. Moreover, SYSTEX Corp. continues to invest in promising cybersecurity startups in Taiwan, hoping to maximize the synergy through complementing resources, to strengthen Taiwan’s cybersecurity landscape.
Create Taiwan’s national team to compete in the global cybersecurity market
Examining from the perspective of the RSA Conference (the world’s largest cybersecurity expo), the participation of various countries has increased rapidly in recent years, seeing new-comers like the UK, Israel, Germany, and others, aside from the host country USA. On the other hand, it is a pity that Taiwanese cybersecurity firms have yet to leverage this international exhibit to engage in the multinational market. SYSTEX Corp. has long observed and analyzed this market, starting cooperation with several overseas cybersecurity firms in 2019 in hopes of integrating a “Taiwan solution” to be brought to the international stage.

COVID-19 transformed the trend
Since we have started our business in Taiwan, we have sponsored the iThome CyberSec events. And, every year as we sponsor the event, I have a chance to write about security trends. This is a good opportunity for me to think about the current IT industry situation and think about how the IT security industry will be in the near future.
Because of COVID-19, 2020 was the year in which many people were forced to work differently than before. And, this is still continuing today. At this moment in February 2021, only 10% of employees are going to the office in our headquarters and others are working remotely. Fortunately in Taiwan, we can work normally although we need to wear masks to go around. But still, there are many industries affected by COVID-19.
Recently, I have noticed some changes caused by COVID-19. I noticed that business society has become more digital friendly. Previously, not only in Taiwan but also in Japan, meeting in person was quite a must for many companies so that our sales members always needed to go to customer places. However, there are more companies accepting online meetings recently.
Since business is a series of transactions between two entities(or companies), in fact, there were a lot of tasks which could not transform into digital because business culture did not allow it. No matter how much your company would like to transform a task into digital, if the opponent entities such as companies or government institutions would not accept in a digital format, digital transformation was not possible. Signing contracts or sending invoices are some examples of these. But now in Japan, there are several big IT companies declaring that they will only sign digitally for the contracts between companies.
I’m starting to see some rising trends that digital transformation is pushed forward by the transformation of business society becoming digital friendly.
Basics of digital transformation(DX)
It is obvious that a company needs profit to grow their business. But, how are the profits made? Simply, profit is the positive gap between revenue and cost. It also can be said as the gap between input and output. Less input with greater output is the key to maximize profit. And, productivity is the amount gap between input and output.
By adopting IT, we have replaced many of manual works to be done in digital. By replacing tasks to digital, we can have the same output with less input. For a simple example, compare searching a person in the physical directory and data in a spreadsheet application. In the physical directory, you need to look for a name by looking at each page but in the spreadsheet, you can search and jump to the person you would like to see. I believe it is obvious that there is less input for searching in spreadsheets.
Digital transformation(DX) means not only replacing manual tasks into digital but also replacing old digital technology to updated digital technology for better productivity. Therefore, how digital transformation(DX) is different from IT-nization(IT化) is that digital transformation means not only “manual-digital” transformation but also “manual-digital-digital” transformation. Adopting CRM systems instead of managing customer data in spreadsheets is one of examples of digital transformation. In any cases, the purpose of digital transformation is to maximize productivity with updated digital technology.
“Best-of-Breed” can be the key for a better productivity
American psychologist, Adam Grant shows in his book “Originals: How Non-Conformists Move the World” that people who used Chrome or Firefox as their browser are likely to stay at their jobs longer than people who used Safari or Internet Explorer. Plus, they were people more productive with less likely to miss work. This is not because Chrome and Firefox are better browsers but those people who used those browsers had the mind to explore and chose other browsers than default to make better performance.
This means, the one who explores for a better solution will have better performance. And, this fact can apply to a company also. A company which explores for a better productivity solution will have more chances of growth in their business.
“Best-of-Breed” strategy is to choose the best product which meets your business requirements. Compared to this, there is an opposite strategy called “All-in-One” or “Best-of-Suite”. “All-in-One” strategy is good to start where you are not familiar with new tools. But, to improve productivity, after understanding the tool, I believe switching to “Best-of-breed” strategy will provide more chances to grow.
IT manager transformation
About 10 years ago, I was in charge of IT in our headquarters working on adopting cloud email systems to our headquarters. At that time, most of my job was to maintain existing servers to make sure servers were running properly, other than to support IT on our employees. Today, our IT manager of headquarters spends most of time finding or trying “Best-of-Breed” products for better productivity. Since all of our systems are now all based on SaaS, our IT manager has no servers to maintain. Although, supporting our employees in IT remains the same, the job description of our IT manager has changed significantly. I feel digital transformation(DX) will also transform how the IT department of a company needs to be.
What is security harmonization
Compared to the “All-in-One” solution, many say that the disadvantage of “Best-of-Breed” products is that they are less capable to be integrated. However, “Best-of-Breed” vendors know that they will only cover certain tasks so that they will add more functions for integrations. Plus, there are vendors who provide solutions to integrate so that integration will be easily done. Therefore, I believe integration is not that big of an issue. In this meaning, our product HENNGE One Access Control can be said as one of integration solutions which will provide a single sign-on feature for different “Best-of-Breed” products.
Even if we say “IT security” in a simple way, there are different aspects. Preventing malware infection, backup data to protect data from mismanupulation of employees and protecting servers from DDoS attacks are all security issues but need different technology to solve. From this, we can say the “Best-of-Breed” strategy also works for the IT security area.
I’m using the term “harmonization” to describe smooth integration between different products making the best solution as a whole. And, “security harmonization” means to integrate multiple solutions to achieve a rigid security.
Security harmonization with HENNGE One
In order to have continuous growth, having high productivity is important. And, improvement of productivity can be achieved by the “Best-of-Breed” strategy making business operations as efficient as possible. In addition, HENNGE One Access Control can be one of integration solutions which provide a single sign-on feature with higher and unified security level.
Now, to present the beauty of security harmonization, let me show an example using HENNGE One Access Control. HENNGE One Access Control is a solution which will provide a secure single sign-on feature for multiple cloud services. And, HENNGE One Access Control will prevent unauthorized access to your cloud services.
The key to prevent unauthorized access is to make sure the person is the one authorized to sign-in. Today, the most common way of sign-in is by ID and password. However, ID in most cases is an email which can be easily assumed. And, there are always a certain number of people who will set easily predictable passwords. As a result, many think ID and password are not enough and multi-factor authentication becomes popular as a more secure way to sign-in. In multi-factor authentication, usually the system will send OTP(One Time Password) to make sure the person signing-in is the person who owns a registered mobile device. This is quite a secure way to sign-in, but the sign-in process becomes quite complicated.
Today, most mobile devices have biometrics sign-in features such as using fingerprint or by face recognition. This means, the person successfully login to the device can relate to the person who owns the device. HENNGE One has a product called Device Certificate which is used by installing a digital certification key to the device. Since a digital certificate is related to a user so that HENNGE One will allow the user owning the device to sign-in using the digital certificate. Although, HENNGE One doesn’t have any biometric authentication function, by combining a biometric authentication feature of a device to sign-in to the device with device certificate sign-in feature of HENNGE One, the user can harmonize the solution as if user can single sign-on to multiple cloud services by the biometric authentication to the device. I believe this is a quite secure way to sign-in yet maintaining simplicity of sign-in process.
Conclusion
Business environment is constantly changing and we have learned that there are situations where natural disasters such as COVID-19 force us to change our business behaviors. From these facts, I believe the best way to survive in business is to constantly try to improve business operations to fit the current situation. And, I believe this is one of the reasons why people are realizing the importance of digital transformation(DX).
However, since every company has different styles of pursuing their business, I believe there is no single solution which will solve all problems for all companies. Therefore, it is important for each company to explore solutions which will fit their business style. To do so, I believe “Best-of-Breed” strategy is a way which every company can try.
Lastly, during the course of digital transformation, we hope our solution will help companies to harmonize their “Best-of-Breed” solutions for its efficiency and security.

Flowmon’s Unified Digital Performance and Security Solution also retains detailed information about network traffic and presents the outputs in a straight forward and understandable way. The solution collects rich network telemetry data from various sources and analyzes it for any relevant information. Using machine learning, heuristics and advanced analytics, it improves network performance, alerts on incidents and enables early threat response. Although often separate, Network Operations and Security Operations teams share a common goal - a stable and healthy network.
Flowmon can handle on-premise, cloud or virtual environments and will integrate with most solutions out there. The UI is simple and deployment takes 30 minutes. There is no duplicity of effort; just one tool.
Flowmon is a comprehensive platform including everything you need to get an absolute control over the network through network visibility. With Flowmon Probes you will never miss any information about network traffic. Flowmon Collectors are dedicated for collection, visualization, analysis and long-term storage of network statistics. The Collector provides highly scalable data storage and analysis for flow data. A single collector virtual appliance can support very high performance for flow data from 75K fps to 200K fps and also include 2 probes for generates data about network traffic.
We are also proving standalone Flowmon Probe to generate data about network traffic from branch office or network segment.
Flowmon modules extend the functionality of Collector to enable the advanced analysis of flow statistics. The ADS module delivers fast anomaly detection, network behavior analysis and protection against advanced cyber threats. The APM allows you to drive user experience and application value. With DDoS Defender you can protect applications against volumetric attacks. For full-scale IP traffic recording & analysis, IT professionals can rely on Flowmon Packet Investigator.
For Complete network visibility - Understanding of what is happening in the network is a key to ensure the smooth running and security of any modern organization. Use its powerful features to get absolute control over the bandwidth utilization, optimize network/application performance, troubleshoot quickly and keep the network protected against modern cyber threats.
For Dominance over cyber threats - How do you protect your systems and data against threats bypassing traditional solutions such as firewall and anti-virus?
Flowmon ADS (Anomaly Detection System) is utilizing sophisticated network behavior analysis, an advanced artificial intelligence based on machine learning, it permanently observes and analyses data communication seeking anomalies and revealing suspicious behavior.
For Protection against DDoS attacks - Flowmon DDoS Defender is a scalable anti-DDoS solution. It leverages statistics from routers or dedicated network probes with an advanced network traffic analysis for realtime detection of volumetric attacks led against HTTP/HTTPS and systems. It provides the state of the art detection of DDoS, deep understanding of attack characteristics and a full-range of methods for successful attack mitigation.
For Application performance monitoring - What if your customers face a slow response of your business application? struggling with errors when working with internal systems? Or detect an error and the root cause? The solution identifies performance problems, reveals root causes and provides a deep-insight diagnostics to drive user experience and application value. With no agents on servers, no changes in configuration.
Our solution advantage is to provide many task in one platform.
Network Visibility - Troubleshooting, capacity planning, bandwidth monitoring, drill-downs, reporting.
Network Security - Network Behavior Analysis & anomaly detection for proactive security approach.
DDoS Protection - Volumetric DDoS attack detection and mitigation orchestration.
Network-based APM - Application Performance Monitoring for real user experience measurement.

The rise of virtual and digital banking brought along great benefits for consumers by making banking services more efficient through the internet and mobile apps, which however inevitably became a major target for criminals. Therefore, cyber security is of crucial importance to the digital financial industry.
The Taiwan Stock Exchange Corporation has weighed in on this topic, and stated that
“for strengthening the cyber security in stock transaction, it’s required to execute relative cyber crime preventions.” For example, stock dealers need 2Factor authentication when placing orders. The president of Changing Information Technology, Mr. Anderson Yang, has argued that the convenience brought by internet transactions should not be thwarted by overcomplicated methods of 2Factor authentication. Fingerprint recognition software is a perfect solution for financial institutions who wish to implement efficient and easy authentication of digital identities.
Fingerprint validation is just one of the methods in Changing Information Technology’s ID Expert security package, which constitutes a comprehensive solution for dynamic authentication including multiple tokens tailored to users’ scenarios and security requirements. ID Expert contains both software and hardware tokens to display a One-time-password (OTP), continuously changing passwords to strengthen security and offer efficient 2Factor authentication.
Additionally, ID Expert allows to monitor and analyze records of access through logs of successful and failed logins. Statistical graphs and notifications aid the user in examining and building cyber security.
Besides offering authentication techniques, our company also offers superb methods for preventing the leakage of confidential data. Corporations exchanging data with flash drives are especially vulnerable for transmitting viruses and trojan horses in between network nodes. uSAFE management system protects flash drives and allows corporations to set up validation rules by restricting certain user’s rights and by limiting USB plugs, thereby being customizable customers’ needs.
Convenience is an advantage of digitization, but at the same time carries the risk of data breaches. The fundamental principle of our cyber security solution is to enhance digital identity validation while strengthening flash drive management to prevent data leakage. These two elements allow to improve efficiency and efficacy, while also achieving cyber security.
Mr. Anderson Yang and Changing Information Technology have been dedicated to cyber security for twenty years, and thereby built expertise in identity authentication, biometric authentication, e-signature (digital signature or e-sign), smart cards, mobile certificates, blockchain technologies, OCR, and many more. These tools are crucial for the further development of the Fintech sector. It is our mission to bring you security and convenience – implementing security and monitoring tools customizable to your need, while simultaneously retaining ease of use.

In 2020, all trends have undergone different changes due to the COVID-19, the digital transformation is which has changed people's lifestyle and work mode, and the focus is information security, gradually The development of information security development is directly transferred from trust to zero trust, and the highest principle of zero trust-"no trust, only authentication." Every access request must be fully verified, and only after authorization and encryption can access rights be granted. Only in this way can we more effectively adapt to the complexity of the modern environment, and protect people, devices, applications, and data at any time and place through mobility and digitization.
The goal of Zero Trust is to strengthen and ensure data security within the organization through various control methods by restricting users' rights and access risks. Therefore, the development of digital identity security in response to digitization follows. Including identity verification and identity management, data sensitivity, application, and device status access policies have become important factors for digital identity security and the key foundation for zero trusts.
In particular, one of the policies issued by the Financial Services Regulatory Commission in 2020: from 2021, bankers need to replace OTP with FIDO as the beginning of zero trusts; and FIDO is a part of digital identity verification. In identity verification, FIDO and SSO must be fully integrated, and privilege management must be added in order to effectively achieve information security control, which is also the key basis for zero trusts.

Kevin / Engineer
Do not discuss too much technology (the information security experts who are better than us are really too many at the CyberSec)
We need to borrow the precious time of your visit to visit our booth to understand the company's thinking and plans. We hope to guide everyone to plan and execute the company within limited resources to strengthen information security. Let the attacker give up the attack then the implementation is successful.

Currently we are facing not only a single hacker but a whole APT hacker group. We are not able to prevent hacker’s intrusion anymore. Unfortunately we are always been noticed that “we have been hacked” by incident happens. The only way we could improve our information security is take the initiative to understand our potential risk.
*Red Team Assessment*
Can we protect the most valueable once we are hacked? Red Team assessment can offer full-scopes, simulate the real-life threat actor, and against with Blue Team to validate the unknown weakness of enterprise.
“Penetration Test”
Penetration Scanning tool is a rigid tool, but the hacker is live with thousands of unpredictable minds. The way we can discover hidden vulnerabilities is relying on the white-hat hacker to perform the advanced penetration testing, so we can actually understand our risk and know how to fix them.
“Managed Detection & Response”
Our professional security consultant are expert on handling hacking incident, we can react to APT challenge before the incident with our MDR service, and provide immdiately response plan to prevent incident happens.
“Vulnerability Assessment”
There is always a security flaw that could be lead to be exploit but we never know, we could perform vulnerability assessment periodicity to find out vulnerabilities which we did not noticed, and our professional consulting service could also provide the most suitable solution for further improvement plan.
“Information Security Diagnostic”
Based on our consultant’s unique user-site experience, we will review the rationality of network / system management architecture, firewall policies and router ACLs to check the correctness of every rule. We will also do a risk assessment of current infrastructure against hacker’s intrusion and provide recommendations for improvement.

IGEL OS
IGEL OS is Linux-based endpoint operating system for simple, smart, and secure endpoint control and optimization. IGEL OS turns any compatible x86 device into a secure IGEL-managed endpoint. The major function includes the following
Hardware-agnostic – runs on any compatible x86 64 bits device.
Built-in security – built on highly secure Linux, multi-factor authentication, smart cards, trusted execution.
Commitment to lockstep firmware support for Citrix, VMware, Microsoft 4x per year
Support for a vast array of partner technology interfaces and protocols (100+ strong and counting)
Universal Management Suite (UMS)
UMS and its graphical user interface make it easy for a non-expert to control and manage from just a few to tens of thousands of IGEL software-defined endpoints with minimal training.
In addition to making end user computing management massively scalable yet easy, UMS features simple cloud-based endpoint software licensing where licenses can roam between any compatible x86 devices, and also Includes
High availability
Workspace Edition includes a high availability option to help ensure continual operation of the Universal Management Suite even if the primary server should become unavailable for any reason. This can prove to be extremely beneficial in larger configurations of thousands or even tens of thousands of IGEL software-defined endpoints.
REST API
Workspace Edition also includes a REST API to allow for easy integration of IGEL UMS with existing management, reporting, and trouble ticketing systems. Often a requirement in many enterprises, the Workspace Edition REST API makes it easy for organizations to exchange information between their IGEL-powered end user computing environment and other software systems.

Cyber-attacks present a growing threat to businesses/enterprises, governments, and individuals all over the world.
There are a lot of cyber-attacks happened to large enterprises in Taiwan in recent years as well.
Then, you thought these large enterprises didn’t prepare an specific security team or professional security software & hardware to protect cybersecuity?
Obviously the answer is No. Hackers still targeted and attacked them which caused the huge losses.
However, we found many small and medium enterprises or e-commerce customers believed that their company scale is small, hackers would not attack them, they may ignore the risk of cybersecurity.
Well goes a saying:「An ounce of prevention is worth a pound of cure」which means you may need spend more money & time to recovery, until everything back to normal when you suffer from cyber-attack by hackers.
There are a lot of targeted threats is increasing recently, such as DDoS attacks, malware, ransomware, data theft and phishing, hackers know how to avoid traditional security measures, it leads to quite severe problem. Hackers may often invade the server to obtain the confidential information & to encrypt files on servers.
However, if you don’t realize the way of thinking of hacker, you will never know how to defense and against hackers. In addition, it is useless to install the inappropriate product of cybersecurity. Therefore, it is a trend to understand hacker to find the potential risk to avoid the cyber-attack.
Website is a service which combines operating systems, server environments, applications and databases etc. We should consider the whole protection strategy of cybersecurity.Be an information security professionals we are responsible of customer’s cybersecurity protection, we conducted updates of version and patch defenses anytime to avoid the vulnerabilities.
In recent years, there are a lot of enterprises realize the cybersecurity is quite critical in Taiwan. We know that is a big challenge in the future. You need think like a Hacker. We will try our best for small and medium-sized enterprises to provide a variety of security tools to assist them(SSL certificates, vulnerability scanning, WAF、DAF database firewall、code review, EDR , DDoS Protection etc.) which could help users to against or defense hackers through our professional skills in the field of cybersecurity.

Mobile security incidents have been reported frequently in recent years, usually because employees use mobile phones steal secrets. Whether it is taking photos or saving data in USB storage, it is easy to take away the company's internal confidential information and cause a great deal of business loss. Faced with such a difficult problem, enterprises need a MDM(mobile device management platform) solution effectively control mobile devices to achieve a balance between ensuring corporate mobile information security and improving mobile productivity.
SkyMDM - MDM solution of XCome mainly includes:
(一)Basic function:
1.Mobile device management(MDM).
2.Wi-fi and network management.
3.Information security management.
4.Location service and tracking.
5.Mobile application management(MAM).
(二)Advanced application:
1.Monitor and alarm center:
(1)Dashboard.
(2)Report and Log management.
(3)Event alarm.
2.FOTA Management(Requires customized mobile device): Device Firmware update management.
3.Dual mode:
(1)Divide apps into work area and personal area.
(2)Data in Work area can’t copy paste to personal area.
(3)Dual mode apps management and runtime permission control.
4.Geo-Fencing:Geo-Fencing control the device specific functions in specific location.
XCome completed the first set of customized MDM solution(Customized SkyMDM) in 2016 and launched SkyMDM(standard platform) in October 2018, which includes Cloud and On Premise versions. With deep accumulation of R&D energy and localized professional services, SkyMDM was successfully adopted by Taiwan's international semiconductor manufacturer, government organizations and well-known companies in Taiwan, China, Japan, and France. It enables enterprises to more quickly and comprehensively manage mobile devices through a single platform, and to improve work output and efficiency without leakage of data.

Gartner’s recently released 2020 versions of the Magic Quadrant for Cloud Access Security Brokers (CASB) and the Magic Quadrant for Secure Web Gateways (SWG) tell us a lot about where both markets are headed. Data and users increasingly reside and work in the cloud, the global pandemic has accelerated digital transformation in unprecedented ways, and the march is on toward the Secure Access Service Edge (SASE) future Gartner first predicted in its 2019 paper, “The Future of Network Security Is In the Cloud.” As the status quo of security inverts from the data center to the user, CASB and SWG increasingly will be the same conversation, not separate technology markets.
In other words, will there even need to be separate CASB and SWG magic quadrants in the future? At Netskope, we don’t think so.
Source: Magic Quadrant for Secure Web Gateways (SWG), Magic Quadrant for Cloud Access Security Brokers (CASB)
There are four key transformations at play, including networking, security, applications, and data. Each has an impact on the required capabilities for CASB and SWG in the context of SASE architecture.
- Networking transformation reduces backhauling, hairpinning, and latency to provide direct to cloud access between users and apps. Remote working is at an all-time high and is predicted to remain well above pre-pandemic levels for the foreseeable future. Users are embracing direct-to-cloud access as opposed to using VPNs and MPLS networking to backhaul to central office egress points for web and cloud services. The many positives for this transformation include a reduction in MPLS and VPN expenses, a simplified environment, and an improved user experience for web, SaaS, and cloud services.
- Security transformation reduces data center, office, and branch office security appliances, moving to a cloud secure access edge with a single pass inspection of user traffic for web, managed SaaS, unmanaged SaaS (Shadow IT), public cloud services, and custom apps in these cloud services. These five types of user traffic all require data and threat protection with granular policy controls by user, group, or OU, and by app, instance, activity, data, and other contextual variables. The givens for security transformation are TLS traffic inspection, Zero Trust Network Access (ZTNA) to data and resources, plus the ability to support any user, device, or location.
- Application transformation migrates apps from the data center to new SaaS replacement choices, new or redesigned custom apps architected for the cloud, or the lift and shift of legacy apps to cloud-hosted virtual machines. SaaS app adoption has nearly doubled year over year from an average of 1,295 apps per organization in 2019 to 2,415 in 2020 based on Netskope Research Labs. The key point for app transformation is less than 2% of these apps are managed by IT with administration rights. The rest are freely adopted by users and business units making Shadow IT a growing security risk.
- Data transformation migrates data out of the data center into apps and cloud services where most of the data resides, however, data exposure happens via boundary crossings into personal instances of managed apps, unmanaged apps (Shadow IT), or data shared via collaboration, social, and web activity. Organizational leaders managing data protection and risk often track this transformation in cloud risk assessments with a focus on Shadow IT and app profile risk ratings. The net result is driving new use cases to control unintentional or unapproved data movement, protection of data and IP from cloud and web-enabled threats, plus providing granular policy controls based on data context to apps and cloud services with data protection and advanced DLP.
None of these four transformations favors a singular focus on CASB or SWG.
The market has generally viewed Cloud Access Security Brokers (CASB) for managed apps and cloud services using an API deployment working out of band to analyze data-at-rest. Associated cloud security solutions also include API-based cloud security posture management (CSPM) and cloud workload protection platforms (CWPP) for managed cloud services. This makes sense for managed apps and cloud services controlled by IT, however, business units and user-led adoption of Shadow IT are a runaway train that needs to be addressed, alongside personal instances (vs. company instances) of managed apps users also access. A SASE architecture requires inline data context, shifting the emphasis for CASB solutions going forward.
Putting a singular focus on Secure Web Gateway emphasizes web threats via an inline proxy solution with advanced threat defenses including pre-execution analysis, sandboxing, machine learning analysis, and remote browser isolation. Given the internet has been the leading source of threats, this makes sense. However, threats are shifting towards SaaS; APWG.org Phishing Trends Report notes the number one phishing target is SaaS/webmail for two years running. SaaS is also being used to attack SaaS, where the leading example is cloud phishing using fake login forms hosted in trusted cloud storage apps.
Even the 2020 Verizon Data Breach Investigations Report (DBIR) highlights the focus on credentials and access compromise for incidents and breaches -- why break in when you can log in? A SASE architecture requires both cloud and web traffic in a single pass proxy architecture with associated defenses for data and threat protection.
Past security and networking leaders are facing new challenges for their existing solutions as the pandemic and increased remote working accelerate disruptive transformation. Consolidation, reduced complexity, and lower costs are benefits of change for the network and security transformations many vendors are quick to emphasize. However, application and data transformations are becoming more disruptive as they drive new use cases, seek to manage risks, and protect data and users. Solutions that address application and data transformations are best suited for the data context of a SASE architecture. In the very near future, the conversation will not be about who has the best CASB or the best SWG, or any other individual piece of a SASE architecture. To get to SASE, it’s time to focus on effective single-pass, integrated CASB and SWG solutions going forward.
ABOUT THE AUTHOR
Tom Clare is a senior product marketing manager at Netskope. His focus at Netskope centers on product strategy with marketing experience in web/cloud proxies, data and threat protection, behavior analytics, network traffic analysis, endpoint protection, endpoint detection and response, deception, and firewalls.

In our advertisements, you can often read that 70 percent of websites are hackable. The sad truth is, however, that every website and web application can be hacked, given enough time and resources.
Hackers are on the lookout for vulnerabilities in your web applications: Shopping carts, forms, login pages, dynamic content are easy targets. Firewalls, SSL and lock-down servers are futile against web application hacking.
While web attacks are not the only type of attacks that may lead to a security compromise, they are one of the most common types along with all forms of social engineering (including phishing) and malware. These types are often also used in conjunction. However, despite the importance of web application security, a lot of businesses still struggle with maintaining it. Here are our recommendations on how to achieve the best security levels:
★Use heuristic detection.
If you only use signature-based detection systems, you are protecting your assets only against script-kiddies. Professional black-hat hackers rely on finding web application vulnerabilities that can only be discovered using a heuristic web vulnerability scanner, such as Acunetix, or manual penetration testing.
★Prioritize web security over network security.
You should realize that there have been very few major breaches in the past years that were due to network security issues, such as the ones associated with SSL/TLS errors. On the other hand, there were quite a few major breaches caused by web security issues from the OWASP Top-10 list such as SQL Injection attacks, Cross-site Scripting (XSS), CSRF, web server and container misconfiguration, etc.
★Eliminate the source of the problem.
If you feel that web application firewall is enough to protect your assets, you should realize that WAF rules can often be circumvented using malicious code and well-crafted user input. By using a WAF with no other measures, you are not eliminating the source of the problem but only applying a temporary band-aid.
Many have argued that you cannot rely on tools alone to find all security vulnerabilities. This is absolutely correct. In all but the most basic security checks, you have to rely on experience and technical knowledge to root out the less-than-obvious vulnerabilities that blackbox scanners simply cannot find. That said manual testing alone is just too time consuming, limited and, for many, downright difficult. A good balance of tools and manual analysis is needed.
The major issue here is that selecting ineffective security testing tools can be a costly venture. I’ve burned thousands of dollars and countless hours on tools that seemed like a good fit based on their tricked out websites and fancy marketing slicks. Talk is cheap so buyer beware. You have to take these tools for a spin to see if they’re going to be a good fit based on YOUR style inside YOUR environment, and based on YOUR business needs.
Whether you’re doing the actual work or just want to make sure your IT and security staff members are using what’s best for the organization, the simple truth is that good security audit tools can and will make a difference. Always remember that there is no one best tool but if you’re smart about your approach you shouldn’t have to spend a lot of money getting the job done right. If you invest a relatively small amount time researching, asking prospective vendors tough questions and actually trying the tools before you buy them, then you can’t lose.
When you choose and use good tools, you’ll know it. Amazingly, you’ll minimize your time and effort installing them, running your tests, reporting your results – everything from start to finish. Most importantly, with a good web vulnerability scanner you’ll be able to maximize the number of legitimate vulnerabilities discovered to help reducing the risks associated with your information systems. At the end of the day and over the long haul, this will add up to considerable business value you can’t afford to overlook.
Acunetix is not just a web vulnerability scanner. It is a complete web application security testing solution that can be used both standalone and as part of complex environments. It offers built-in vulnerability assessment and vulnerability management, as well as many options for integration with market-leading software development tools. By making Acunetix one of your security measures, you can significantly increase your cybersecurity stance and eliminate many security risks at a low resource cost.
“Automate and Integrate Your Vulnerability Management”
To save resources, ease remediation, and avoid late patching, enterprises often aim to include web vulnerability tests as part of their SecDevOps processes. Acunetix is one of the best DAST tools for such a purpose due to its efficiency in both physical and virtual environments.
Acunetix integrations are designed to be easy. For example, you can integrate Acunetix scans in your CI/CD pipeline with tools such as Jenkins in just a few steps.
For effective vulnerability management, you can also use third-party issue trackers such as Jira, GitLab, GitHub, TFS, Bugzilla, and Mantis. For some issue trackers, Acunetix also offers two-way integration, where the issue tracker may automatically trigger additional scans depending on the issue state.